In the first part of our practical series, we flip the switch and configure the global retention policy. It forms the indispensable foundation of your compliance strategy.
Remember the principle of the “watering can” here: Our goal is an invisible safety net that protects the entire tenant across the board without a user having to click on anything.
The scenario for this guide | We configure a policy that automates the balancing act between German bureaucracy and data protection:
- GoBD (The Duty): We ensure that all emails and Teams messages are stored in an audit-proof manner for 10 years – even if an employee permanently deletes them from the trash.
- GDPR (The Freestyle): We ensure that this data is automatically deleted after the deadline in order to comply with the legal data economy and keep your tenant clean.
- 👉 Mainarticle: Data Lifecycle Management: Data Lifecycle Management
- 👉 tom article: Creating labels
- 👉 tom article: Publishing labels (label policy)
Step 1: Getting started
Before you get started, a technical check: Do you have the necessary rights? A “Global Admin” has access to everything, but Microsoft is strict in the Purview Portal. Often, you’ll need to add yourself to the Compliance Administrator or Organization Management role group to create policies.
- Navigation:
- Go to the Microsoft Purview Portal (
purview.microsoft.com - Go to
Data Lifecycle Management (Datenlebenszyklusverwaltung ) > Richtlinien (Policies) > Aufbewahrungsrichtlinien (Retention Policies).
- Go to the Microsoft Purview Portal (
- Create policy:
- Click New retention policy .
- Give the policy a descriptive name, such as
Global-Retention-Exchange-Teams-10Years.
Tip: Avoid names like “Test-Policy.” Once a policy has been activated, it can be difficult to get rid of in an emergency (see Preservation Lock). Choose a name that clearly describes the purpose (10 years) and scope (Global).

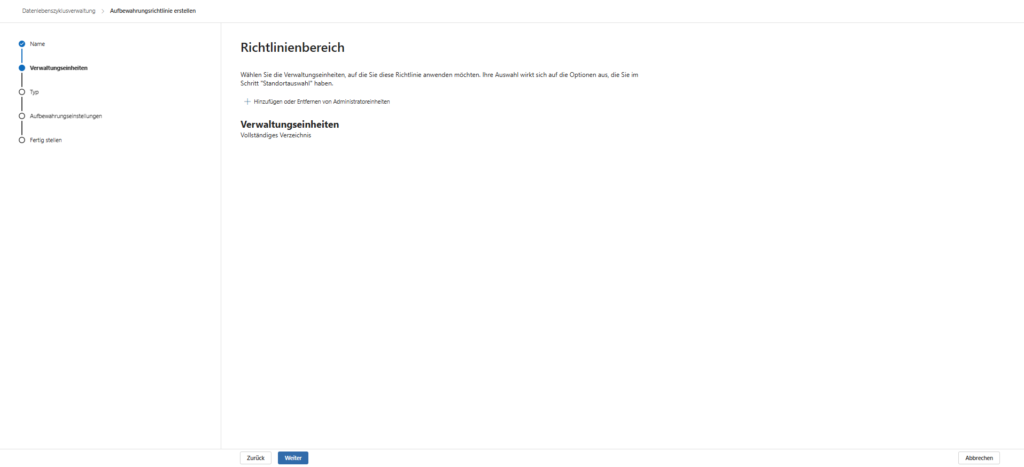
Step 2: Administrative Units
In the second step, Microsoft will ask you for administrative units.
- What is it? This is a feature for large corporations that strictly separate their IT (e.g. “Admin A may only create guidelines for Germany, Admin B only for the USA”).
- The recommendation: Unless you’re in charge of a multinational corporation with delegated administration, leave this setting at the default value of “ Full directory”.
- Click Next.
Step 3: The Type – Static vs. Adaptive (Setting the Course)
This is where you make the most important decision for the maintainability of your policy. Microsoft offers you two ways:
A. Adaptive (The Modern Way | Requires E5)
“Locations can be dynamically mapped with an adaptive scope using attributes… shall be indicated.’
- How it works: You build a query, e.g.
Department = 'Finance'orCountry = 'Germany'. - The advantage: The policy is intelligent. If you create a new employee in the AD tomorrow and give him the “Finance” department, the retention will take effect automatically. You never have to touch the policy again.
- Prerequisite: You need appropriate licenses (E5 Compliance or Information Governance) for the users.

B. Static (The Standard Way | E3 compatible)
“You select locations that contain the content…”
- How it works: You select “All Exchange mailboxes” or pick out individual users/sites manually.
- The advantage: It works with any basic license (Business Standard, E3).
- The disadvantage: For complex exceptions (e.g., “All except management”), you’ll need to maintain the list manually. However, if you create a global policy (“All mailboxes”), “Static” is completely sufficient and requires little maintenance.
Our choice for this guide: Since we want to build a global basic protection for the entire company, we choose Static. This covers all licenses and protects everyone across the board.

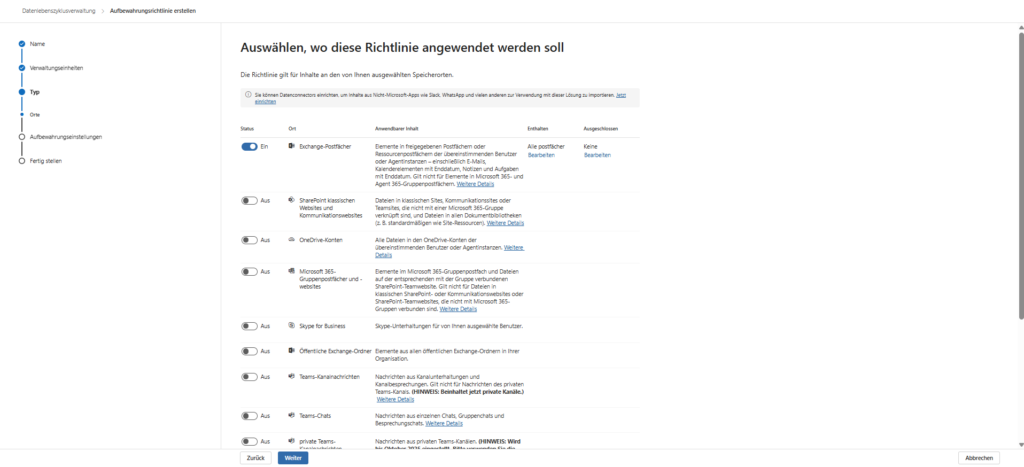
Step 4: Select locations (Where does the protection apply?)
After we have decided on “Static”, Microsoft shows us the list of all available services (locations). This is where we define the scope.
Activate the switches for the services that you need to archive in an audit-proof manner:
- Exchange Email: Enabled. Includes all user mailboxes.
- SharePoint sites: Enabled. Includes document repositories in SharePoint and the files in Microsoft Teams (since these are technically in SharePoint).
- OneDrive accounts: Enabled. Important for employees’ personal business documents.
- Teams chats & channel messages: Enabled. Secures the actual chat communication.
⚠️ Important note about Teams: Many admins think that everything is done with the tick in “Teams chats”. Wrong!
Optional: Enable ‘Microsoft 365 Groups’ if your teams also use the group mailbox features (shared calendar/inbox in Outlook) intensively.
- Chats & Text: Backed up via the Teams Chats and Teams Channel Messages toggles.
- Files & PDFs: Everything you upload to Teams technically ends up in SharePoint or OneDrive. To protect these files, you must also check the boxes for SharePoint sites and OneDrive accounts !

Step 5: Retention Settings (The Logic)
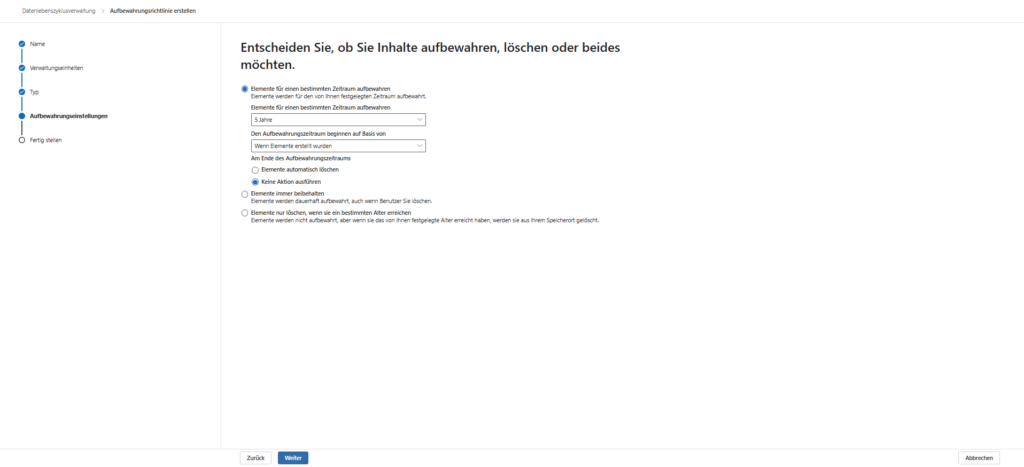
Now let’s define the time span. Microsoft asks : “Decide whether content should be retained, deleted, or both.”
For our scenario, we choose to retain items for a specific period of time.
- Period: 10 years (or Custom).
- Start of the period: Select “ When items were created”.
- ⚠️ Created vs. Modified Here you have to pause for a moment. We usually choose “Created” for the global policy, because this is the only correct date for e-mails (GoBD).
- The risk with SharePoint: If you choose “Created”, an Excel list that was created 10 years ago will be deleted today – even if it is edited daily (since the creation date counts).
- Tip: If you have a lot of these “living documents”, it’s often safer to build two separate policies: one for Exchange (Base: Created) and one for SharePoint (Base: Last Modified).
- ⚠️ Created vs. Modified Here you have to pause for a moment. We usually choose “Created” for the global policy, because this is the only correct date for e-mails (GoBD).
- Action after expiration: Select Delete Items Automatically. This ensures data economy (GDPR) and prevents your tenant from becoming a data graveyard.
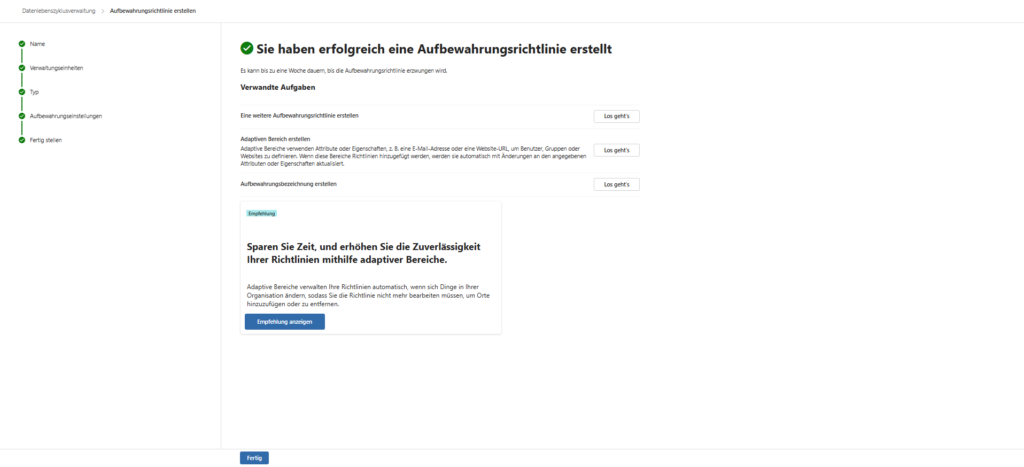
- Click Next and in the last step, click Submit .
Patience is a virtue: After saving, the policy is often set to “Pending”. It can take up to 7 days for it to be fully replicated to all servers and mailboxes.
Step 6: Review & Conclusion
Before the policy is activated, Microsoft will show you a summary of all settings. Take a moment here – careless mistakes are annoying to correct in compliance rules (especially if data is accidentally deleted too early as a result).
Checklist for the last look:
- Is the guy right? (Static vs. Adaptive)
- Are all the places included? (Reminder: Teams files need SharePoint!)
- Is the logic correct? ( Keep for 10 years vs. delete)
- Click Submit .
What happens now (The Patience Game): Don’t expect real-time miracles. The dashboard will initially set the status of the policy to Pending or On .
- Exchange: The guideline usually takes effect within 24 hours.
- SharePoint / OneDrive / Teams: Here, it can take up to 7 days for the policy to replicate and take effect across the tenant.
Tip: As long as the status is not set to “On (Success)”, don’t panic if deleted items don’t appear in the archive yet. The system works in the background.


Preservation Lock: The irreversible vault
We now have a policy that prevents users from deleting data. But what about a “rogue admin” or an attacker who takes over your account? He could simply deactivate the policy. This is not enough for strictly regulated industries (financial sector, pharmaceuticals). They demand WORM memory (Write Once, Read Many). In Microsoft 365, this is called Preservation Lock.
What does the lock do? When you activate this mode, you throw away the key:
- ❌ No one can disable or delete the policy.
- ❌ No one can shorten the period or remove locations.
- ✅ The only thing that works: extend the period or add locations.
⚠️ Warning: NEVER enable the Preservation Lock for testing guidelines! There is no way back – not even via Microsoft Support.
Import-Module ExchangeOnlineManagement
Connect-ExchangeOnline
Set-RetentionCompliancePolicy -Identity "Global-Retention-Exchange-Teams-10Years" -RestrictiveRetention $trueOnly use this if you are legally compelled to do so (e.g. SEC Rule 17a-4). For normal GoBD purposes, the standard policy without lock is operationally more secure.




