Devices are now the new security perimeter. Whether it’s a company laptop or a private smartphone (BYOD), as soon as a device accesses your data, it needs to be managed. Effective management in Microsoft Entra goes a long way towards security and GDPR compliance.



In this section, we’ll harden the “join” of devices and ensure that users don’t accidentally become full administrators on their PCs.
1. Device Settings
This is the heart of the configuration. Here you decide who is allowed to bring devices into your tenant and what rights these users receive.
Path: Identity > Devices > All Devices > Device Settings
Joining and registering Microsoft distinguishes between “Link” (Join, usually company PCs) and “Register” (Register, usually BYOD/private devices).
- Users can link devices to Microsoft Entra: → Selected (or None).
- Recommendation: Limit the full integration of company PCs to IT personnel or specific deployment users to avoid uncontrolled growth.
- Users can enroll their devices in Microsoft Entra: → All (for BYOD) or None.
- Note: This allows users to make private devices (mobile phones, laptops) known, e.g. to gain access to M365 apps.
- Maximum number of devices per user: → 10 (or less).
- Recommendation: A limit prevents “device hoarding” and forces you to clean up old devices.
Security (MFA & Local Admins) Here are the most critical switches for the security of your endpoints.
- Multi-factor authentication… Required: → No (if you’re using Conditional Access) or Yes (without CA).
- Important: Microsoft recommends leaving this switch on “No” and using a Conditional Access policy instead, as this is more flexibly controllable.
- The registering user will… as a local administrator… Added: → None.
- Safety tip: This is one of the most important switches! If you set “All” here, each user is an admin on his PC – a gateway for malware. Select “None” to enforce the principle of least privilege.
- Enable on-premises Microsoft Entra administrator password solution (LAPS): → Yes.
- Explanation: Enables modern management of local admin passwords (see point 4).

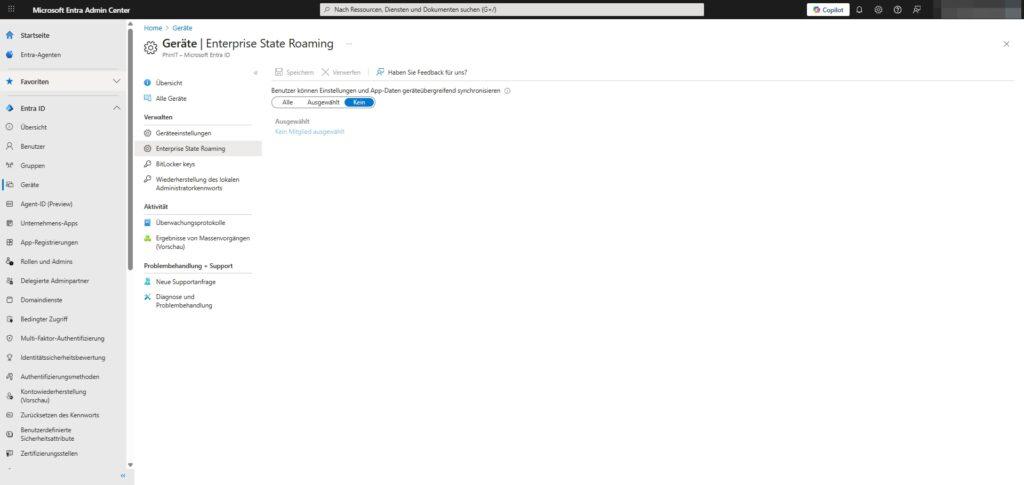
2. Enterprise State Roaming
This service synchronizes user settings (e.g. Wi-Fi passwords, language settings, design) across different Windows devices to the cloud.
Path: Identity > Devices > All Devices > Enterprise State Roaming
- Users can sync settings and app data across devices: → None (or Selected).
- Privacy Notice: From a GDPR perspective and security reasons, caution is advised. It is often not desired that company data (such as app lists) or passwords be synchronized to private, registered devices. If in doubt, deactivate.
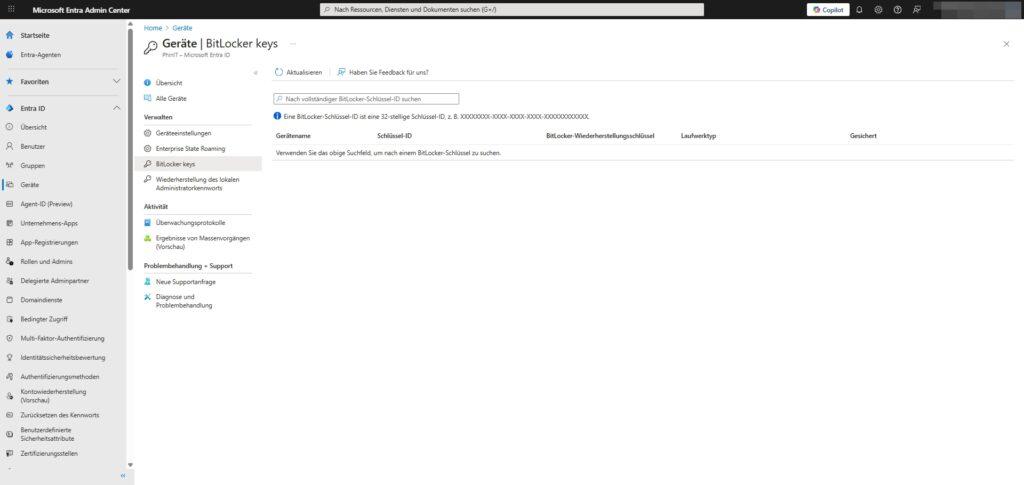
3. BitLocker keys
This is not a settings menu, but your emergency tool. If a user forgets their BitLocker PIN or the hardware is locked, you can find the recovery key here.
Path: Identity > Devices > All Devices > BitLocker keys
- Function: You don’t look for the computer name here, but for the key ID that the banned user sees on their blue BitLocker screen.
- Configuration tip: You have already configured whether users are allowed to retrieve their keys themselves in the “My Account” portal under Device Settings (point 1, at the bottom “Other Settings”).
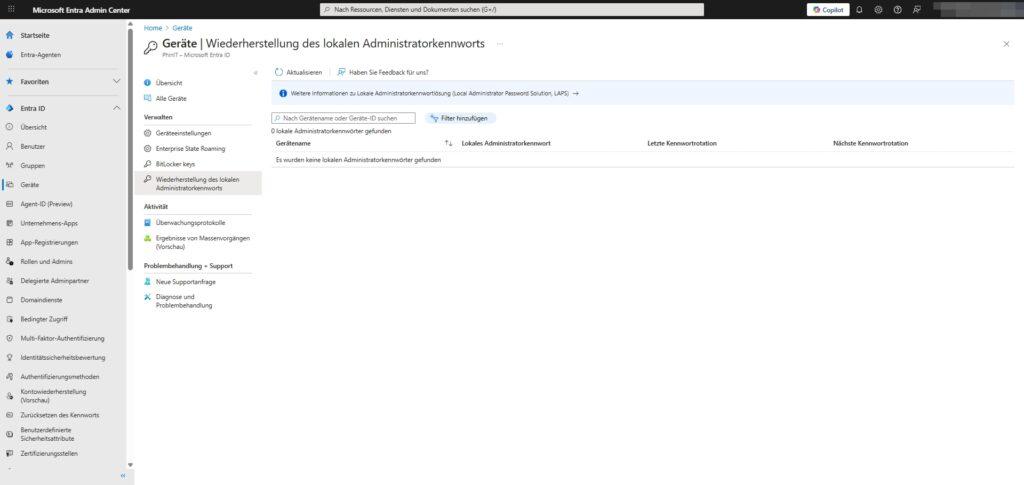
4. Local Administrator Password Recovery
If you have LAPS enabled under point 1, this is the place where you access as an admin. LAPS (Local Administrator Password Solution) automatically rotates the local admin password on Windows devices and stores it securely in Entra ID.
Path: Identity > Devices > All Devices > Local Administrator Password Recovery
- Application: If you need physical access to a device or need admin privileges via remote tool, you can read the current password for the device’s local admin account here.
- Advantage: There is no longer a static admin password in the company (“Summer2025!”) that hackers could grab to move through the network (lateral movement).



Be the first to comment