One thing in advance! Since May 2025, Microsoft has automatically rolled out a “Block device code flow” conditional access policy to all Microsoft 365 tenants. This means that device code phishing is blocked by default without administrators having to take any action themselves.
What is Device Code Phishing?
Device code phishing is a sophisticated attack method that abuses a legitimate Microsoft authentication feature. The “Device Code Authentication Flow” was originally developed to securely integrate devices without a keyboard or with limited input (such as smart TVs, IoT devices) into Microsoft 365 environments.
How does the attack work?
- Phishing bait: Attackers send deceptively real emails or messages that contain a device code
- Victim interaction: The victim is prompted to enter the code on a Microsoft sign-in page
- Feigning legitimacy: Since the code actually comes from Microsoft, the process appears trustworthy
- Gain access: After entering the code, the attacker gains access to the victim’s Microsoft 365 account
- Privilege escalation: With the privileges gained, the attacker can compromise other systems
Why is this method so dangerous?
- MFA Bypass: Device Code Phishing Can Bypass Multi-Factor Authentication
- Legitimate Microsoft URLs: The URLs used are genuine and are not blocked by security tools
- Difficult to detect: For end users, the attack is almost indistinguishable from legitimate processes
- Graph API access: Attackers often gain far-reaching privileges via the Microsoft Graph API
Microsoft’s automatic protection in detail
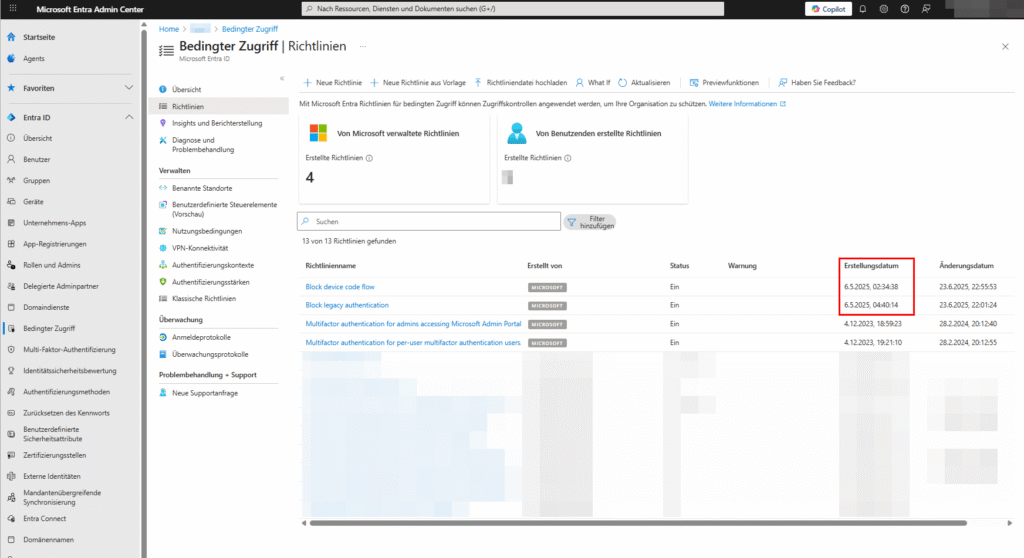
The Block device code flow policy, which is rolled out by default, protects all users from device code phishing attacks. You can view the policy in your Microsoft Entra admin center under Conditional Access | Policies (Conditional Access | Guidelines).
Properties of the default policy:
- Status: Automatically enabled
- Audience: All users
- Applications: All cloud apps
- Action: Block Device Code Flow
When are exceptions necessary?
Although the default protection is excellent, there are legitimate scenarios where Device Code Authentication is needed:
Legitimate Use Cases:
- IoT devices without keyboard/display
- Smart TV Apps for Microsoft 365
- Embedded Systems with Microsoft Integration
- Legacy applications that rely on device code
- Special kiosk systems or digital signage
Device code phishing poses a serious threat to Microsoft 365 environments. The combination of technical protection measures and user awareness is crucial for effective protection.
Conditional Access Policy | Device Code Flow Exceptions
Preconditions
- Microsoft 365 Business Premium, Microsoft 365 E3/E5, or equivalent license
- Global Administrator or Conditional Access Administrator privileges
- Azure AD Premium P1 or P2
Step 1: Open Policy
- In the Microsoft Entra admin center , navigate to > Conditional Access > Policies
- Find the “Block device code flow” policy and click on it
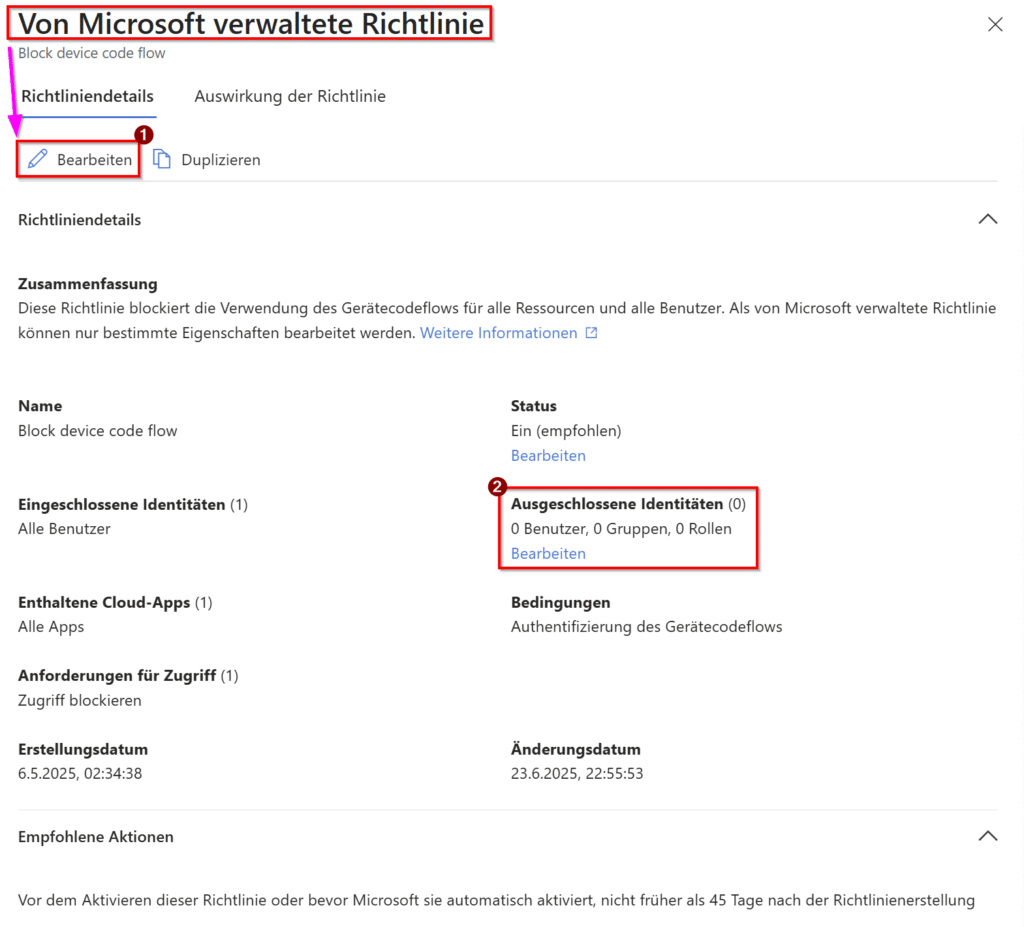
Step 2: Edit Policy
- Click on “Edit” (as shown in image 2, point 1)
Or …
- Scroll to the “Excluded Identities” (as shown in image 2, point 2)
- Click “Edit” on the excluded identities
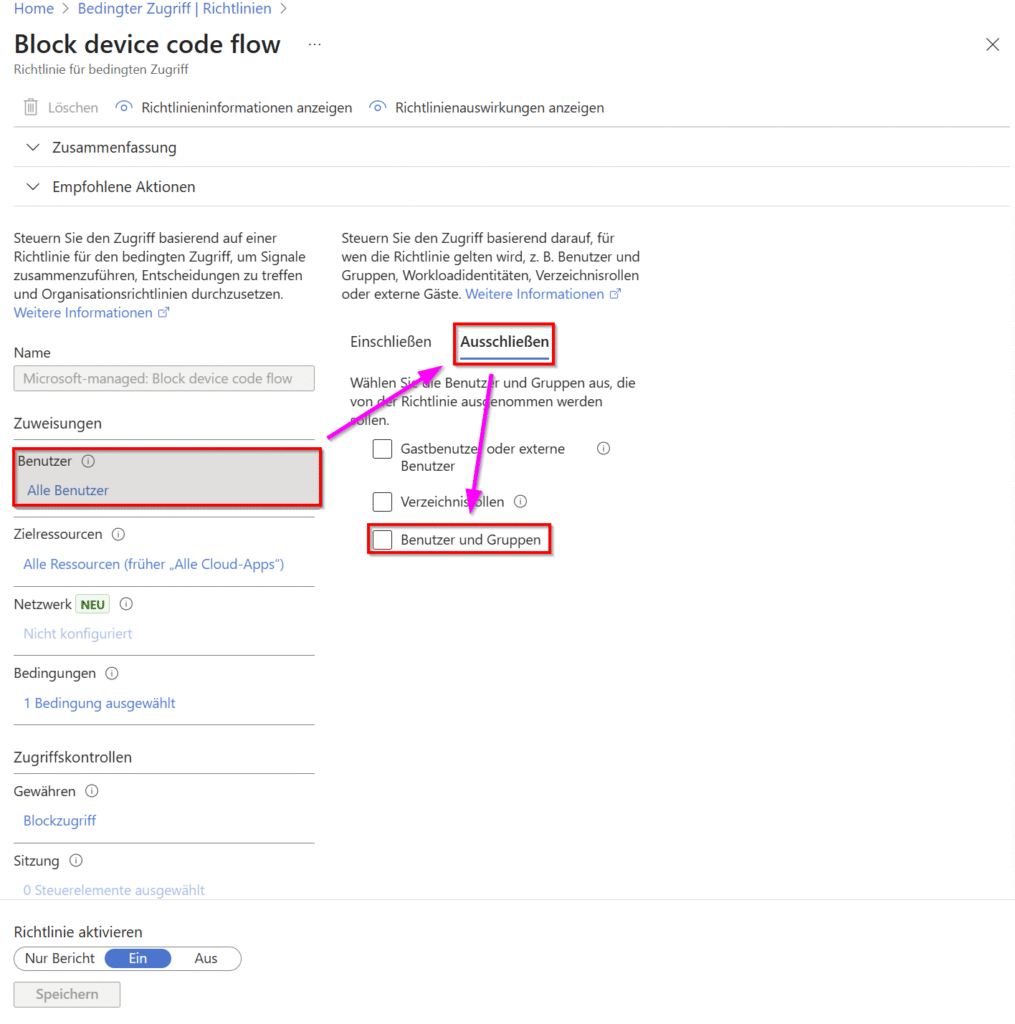
Step 4: Exclude users/groups
- Switch to the “Exclude” tab (as shown in Figure 3)
- Select the “Users and Groups” checkbox (image 3)
- Select the desired users or groups to be exempted from the policy
Step 5: Save
- Click on “Save” to apply the changes
Important note: The policy must be set to “On” for it to become active (see below in Figure 3: “Activate Policy” – “On”).
The excluded users/groups can then continue to use the Device Code Flow while remaining blocked for everyone else.




