– Architecture, application, and best practices for IT administrators
The amount of sensitive data in companies is growing exponentially – and with it the risk. In a modern world of work, where data constantly crosses the boundaries of firewalls and networks, classic perimeter-based security models or pure NTFS permissions are no longer enough.
Here we change the strategy: Identity and Data become the new perimeter.

Microsoft Purview Sensitivity Labels are at the heart of this data-centric security strategy. They allow you to not only classify data, but also attach protection directly to the data object, whether it’s in SharePoint Online, sent by email, or on a USB stick.
Note on licensing:
In this article, we focus on the possibilities of the Microsoft 365 Business Premium license. This already provides you with powerful tools for manual classification and encryption. Advanced features such as fully automated labeling based on content (e.g., “Recognize credit card numbers and set label ‘Strictly Confidential'”) often require an E5 license or the Compliance Add-on. I would like to point this out in the appropriate places.
Preconditions
Before you get started, let’s take a quick check to see if your environment is ready to go. In order for sensitivity labels to work properly, you need the following basics:
- Licenses:
- Microsoft 365 Business Premium: This is our “license” for this article. It allows you to create labels, assign them manually, and encrypt content.
- Office 365 E5 / Microsoft 365 E5 (or compliance add-ons): You will need this if you want to use features such as auto-labeling (automatic classification) or machine learning (trainable classifiers) later on.
- Permissions:
- You’ll need access to the Microsoft Purview Compliance Portal (formerly Compliance Center). At least one of the following roles should be assigned to your account:
- Global Administrator
- Compliance Administrator
- Compliance Data Administrator
- You’ll need access to the Microsoft Purview Compliance Portal (formerly Compliance Center). At least one of the following roles should be assigned to your account:
- Office versions (client side):
- Modern Office versions (Microsoft 365 Apps) already have the client for sensitivity labels built-in (built-in labeling). So you no longer have to distribute separate software or add-ins on the clients.
Architecture and technical functionality
Sensitivity labels are much more than just “digital stickers”. They are part of the Microsoft Purview Information Protection Platform and dig deep into the architecture of your Microsoft 365 tenant. It’s important for IT administrators to understand the three layers of architecture: classification, transportation, and enforcement.
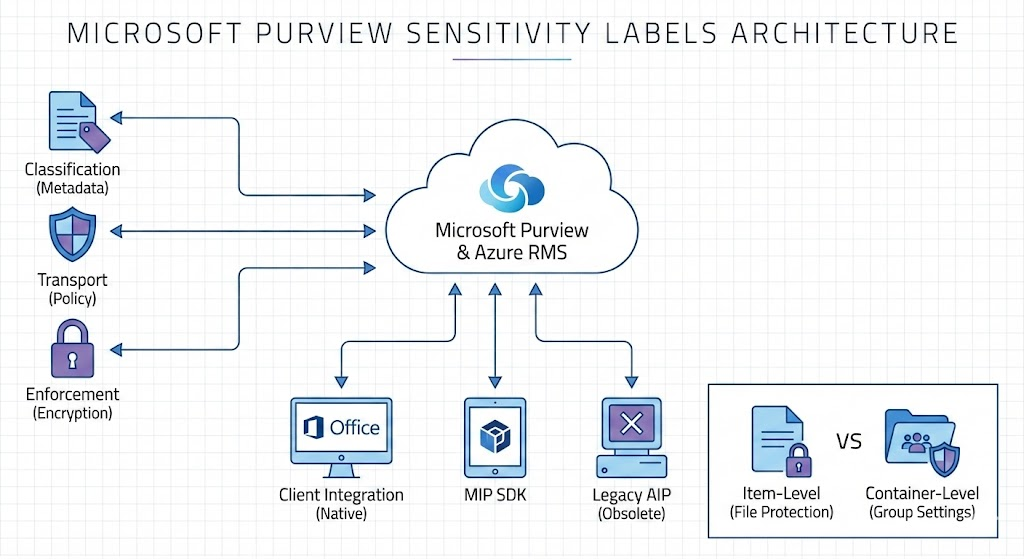
1. The label as an intelligent metadata object
Technically, when used, a sensitivity label writes metadata in plain text to the header information of a file. For Office documents (Word, Excel, PowerPoint), for example, they end up in the Custom Properties as msip_labels.
- Plain Text Metadata: Because the label itself (the tag ID) remains readable unencrypted, data loss prevention (DLP) solutions, third-party apps, or firewalls can also detect the classification level without having to decrypt the content.
- Persistence: This metadata remains permanently attached to the file, even if it leaves the M365 environment.
The Service Layer: Purview & Azure RMS
Behind the administration interface (Compliance Portal) is a complex backend.
- Management Plans (Purview): Here you create labels and distribute them to users or groups via Label Policies (e.g. via Entra ID Security Groups). A policy not only controls who sees a label, but also features such as the default label or the justification when downgrading confidentiality.
- Data Plane (Azure RMS): If a label requires encryption, the service falls back to the Azure Rights Management Service (Azure RMS ). Azure RMS acts as the cryptographic engine. The content is encrypted and provided with a publishing license . This defines who receives which rights (Usage Rights: View, Edit, Print, Export) (authentication via Entra ID).
Important for admins: Even if Microsoft shifts the branding to “Purview” and “AIP” (Azure Information Protection) takes a back seat as a product name, Azure RMS remains the technical engine that regulates encryption.
3. Client Integration and SDK
In order for users to be able to use labels, the software must be label-aware.
- Native integration: In modern Office versions (desktop, web, mobile), the functionality is natively integrated (built-in labeling).
- Practical tip: The old COM add-in (AIP Unified Labeling Client) is obsolete for Office apps. Don’t roll it out anymore and migrate existing clients to the native integration.
- Practical tip: The old COM add-in (AIP Unified Labeling Client) is obsolete for Office apps. Don’t roll it out anymore and migrate existing clients to the native integration.
- Microsoft Information Protection (MIP) SDK: Third-party manufacturers (e.g. Adobe Acrobat, CAD software or cloud security gateways) use the MIP SDK to read and write labels. This guarantees consistent behavior across the Microsoft ecosystem.
Container vs. Item Level
A common misunderstanding lies in the scope of application. Today, we distinguish between two worlds:
| Scope | Description |
| Item Level | The label protects the file or email itself (encryption, watermark, header/footer). The protection travels with the file. |
| Container Level | The label is applied to Microsoft Teams, M365 Groups, or SharePoint Sites . Attention: This does not encrypt the files in it! It controls the container’s settings, such as “Block guest access” or “Allow access only from managed devices”. |
Step-by-step creation and configuration
To use Sensitivity Labels productively, you need to understand the logic of the Purview Compliance Portal. The process follows a strict hierarchy that you should adhere to to avoid configuration errors: Activate scopes -> Plan taxonomy -> Build labels -> Publish policies.
1. Create technical requirements (scopes)
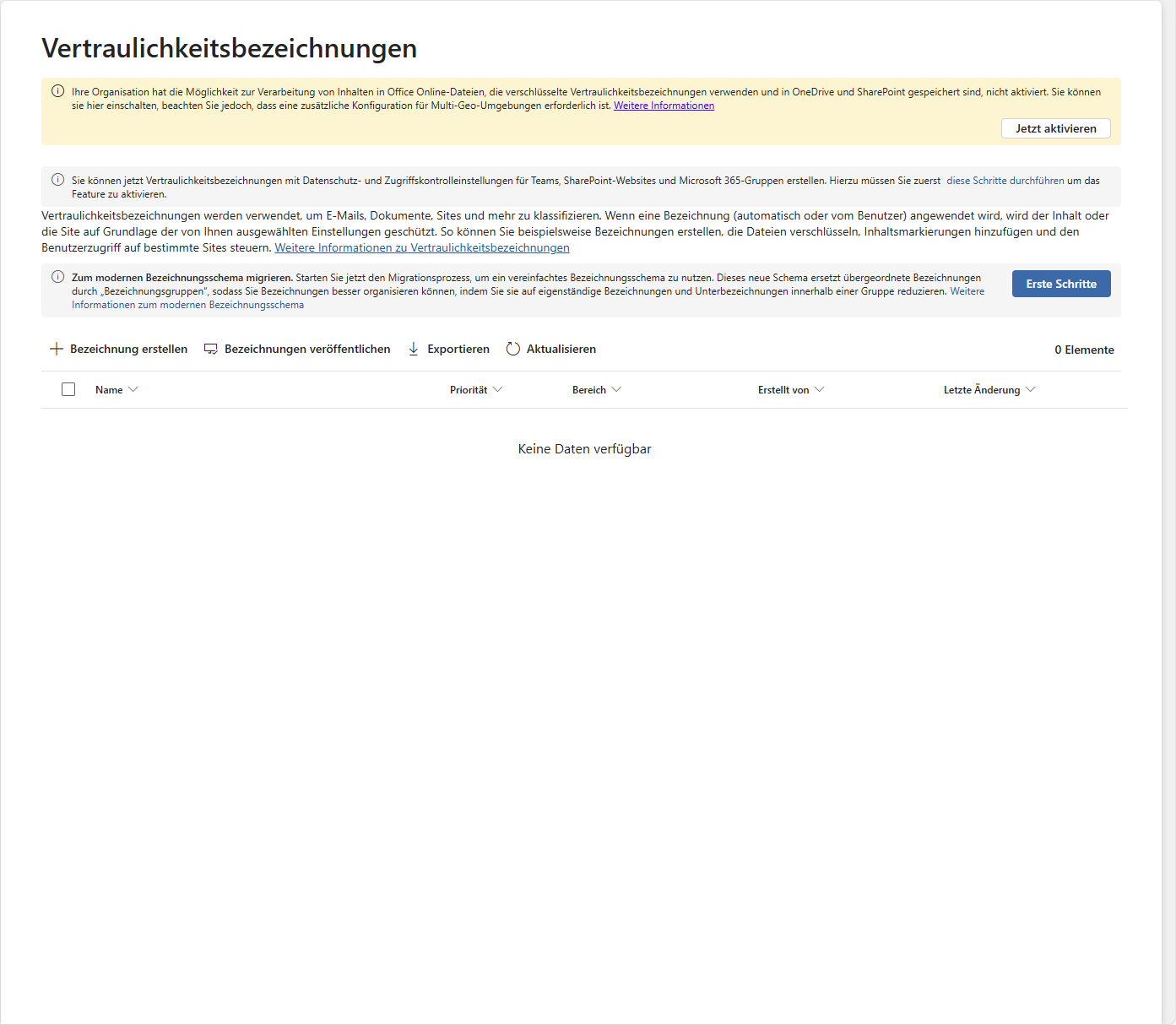
Before you create the first label, you need to make sure that your tenant is even willing to integrate it deeply into the platform. The old button “Activate Unified Labeling” is history. Instead, two features must now be explicitly activated for labels to develop their full potential.
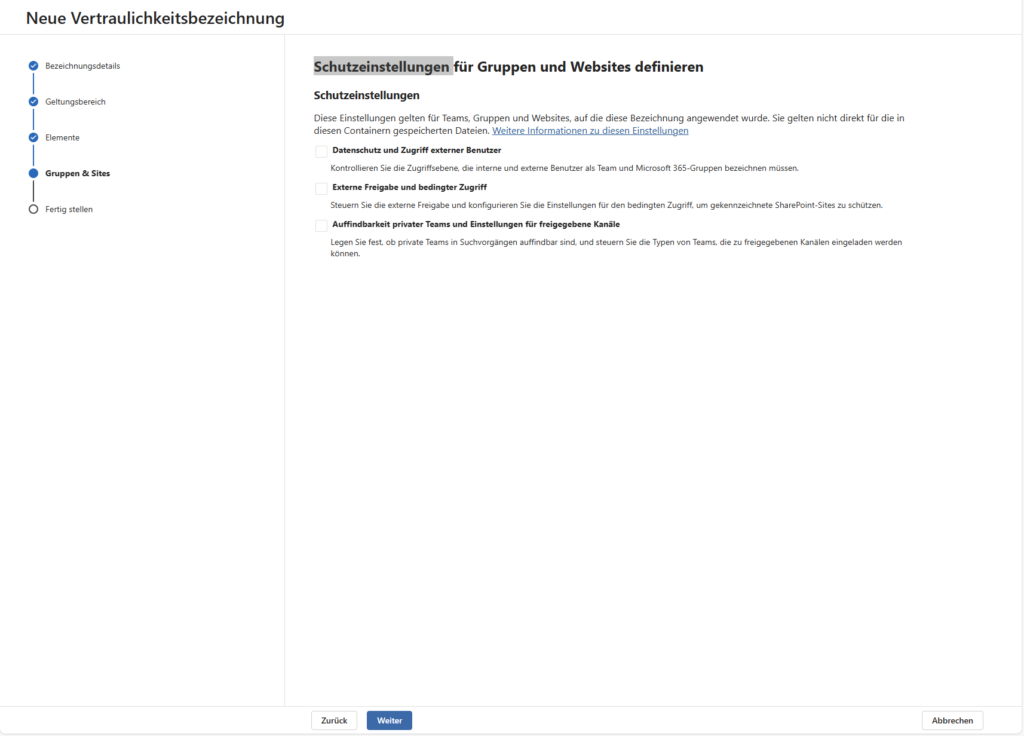
By default, sensitivity labels only “see” files and emails. If you also want to use labels to protect Microsoft Teams, M365 groups or SharePoint sites (e.g. to block guest access to “secret” teams), this feature must be enabled at the tenant level.
- The trail: This is done once in the Microsoft Entra ID Directory setting.
- Attention: Since the old
AzureADPreviewPowerShell module is being deprecated, today it is ideally activated via the Microsoft Graph PowerShell SDK (or via a notification in the Purview Portal, if it appears). Without this step, the tabs for “Groups and Websites” in the Label Wizard will not even appear.
Encrypted files used to be “black boxes” for SharePoint. Search couldn’t index them, and collaborative editing in the web browser was impossible.
- The solution: Enable the “Co-authoring for files with sensitivity labels” feature.
- The effect: Once active, SharePoint Online will be able to read the contents of encrypted files. This is essential for:
- Full-text search: Users can also find documents by content, not just by file name.
- eDiscovery: Compliance Search finds critical content.
- Web Usage: Encrypted Word/Excel/PowerPoint files can be opened directly in the browser and edited simultaneously by several users.
2. The taxonomy: less is more
Before you click in the portal, take pen and paper. A structure that is too complex overwhelms users and leads to them simply choosing the first label that comes along, just to be able to continue working.
Best Practice: Start with a maximum of 3-5 main categories (parent labels). A proven structure is often based on this standard:
- Staff (Private):
- Purpose: Non-business data.
- Technology: No encryption, no logging. Often used to exclude private files from DLP scans.
- Public:
- Purpose: Data that is explicitly intended for the public (website texts, marketing flyers).
- Technology: No encryption.
- General (Internal):
- Purpose: The standard for daily work (memos, internal communication).
- Technology: No encryption (or only visual marking).
- Tip: This is often the perfect candidate for the default label.
- Confidential:
- Purpose: Sensitive projects, customer data, contracts.
- Technology: This is where protection begins. Encryption + access restriction (e.g. “Employees only”).
Pro tip: Sub-labels only if there is a technical difference Use sub-labels (child elements) only if it is technically necessary .
- Incorrect: Confidential -> Finance and Confidential -> Sales if both have exactly the same rights (e.g. “All employees”). That only confuses.
- That’s right: Confidential -> All Employees vs. Confidential -> HR Only . Here, the different permissions justify the subdivision.
3. Creation of the labels (The “What”)
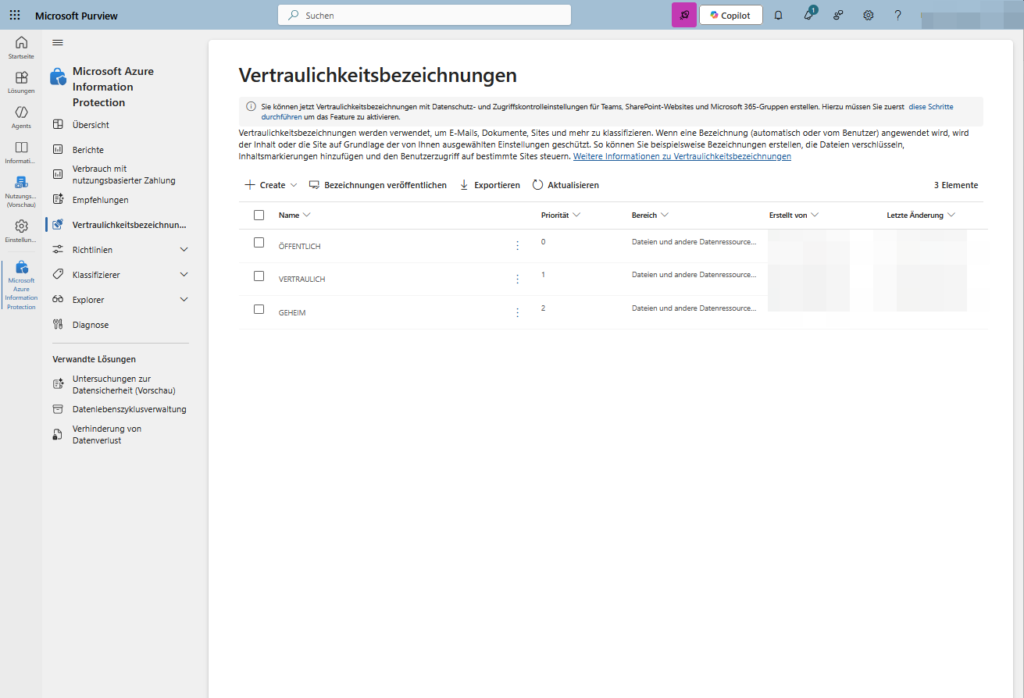
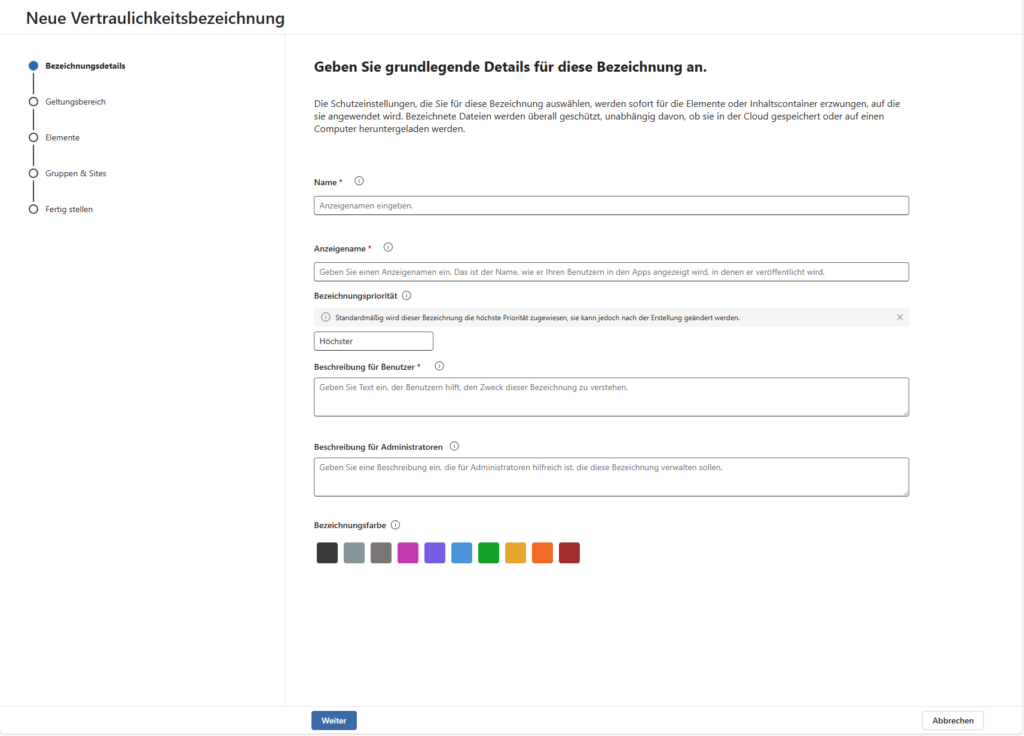
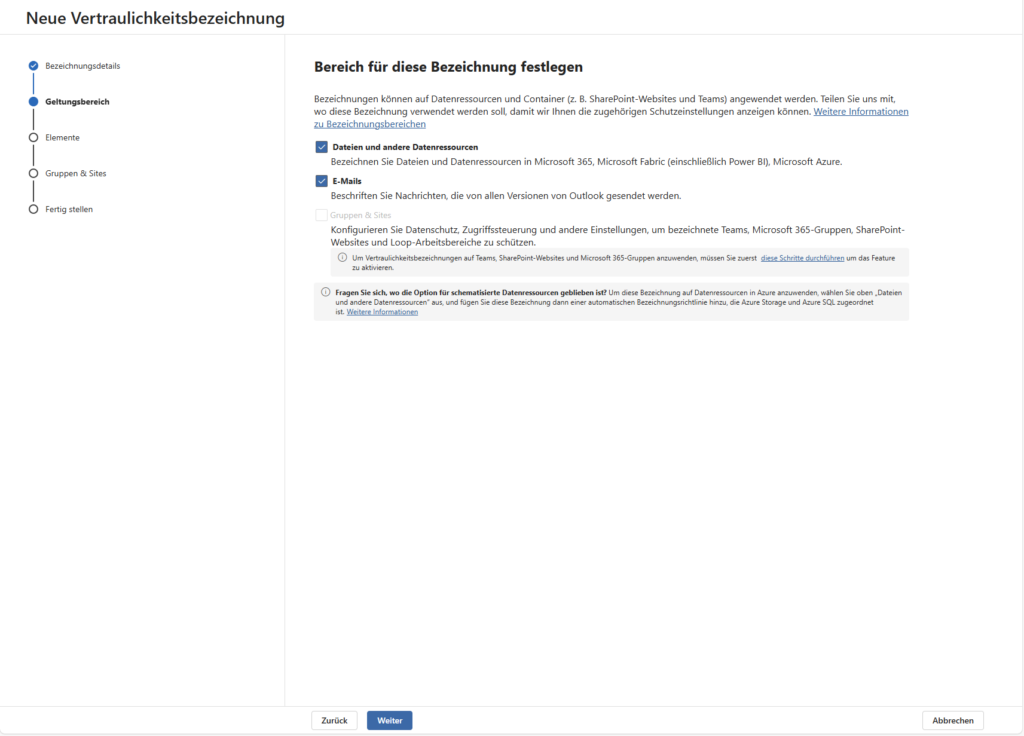
Directly after the basic information, the assistant asks you: “Where should this designation apply?” Here you define the reach of the label. For the beginning, two hooks are usually relevant:
- Items: The label applies to files (Word, Excel, PowerPoint, PDF) and e-mails.
- Groups & Sites: The label applies to Microsoft Teams, M365 Groups, and SharePoint Sites.
- Note: This option is only available if you have met the requirements (see above).
4. Protection settings for files and emails
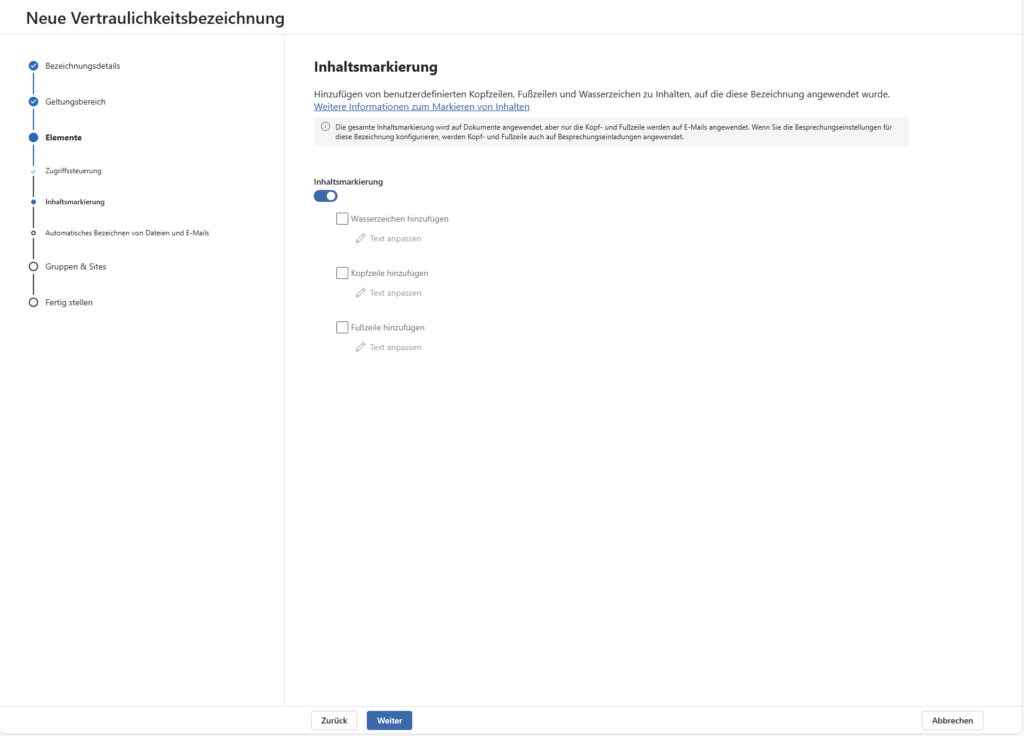
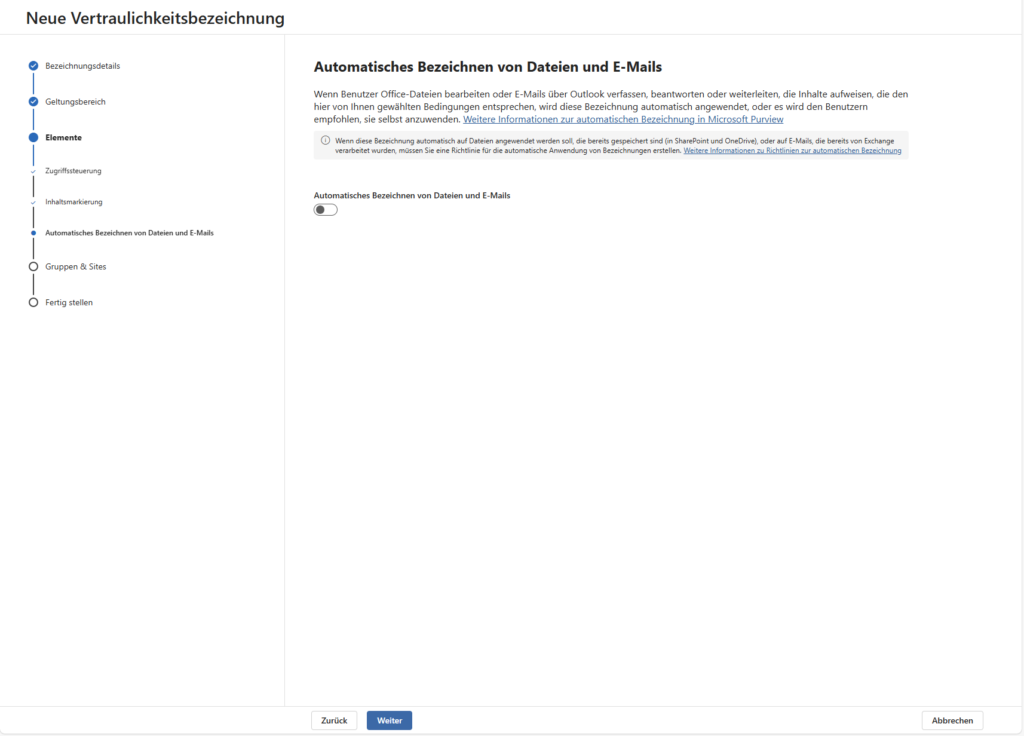
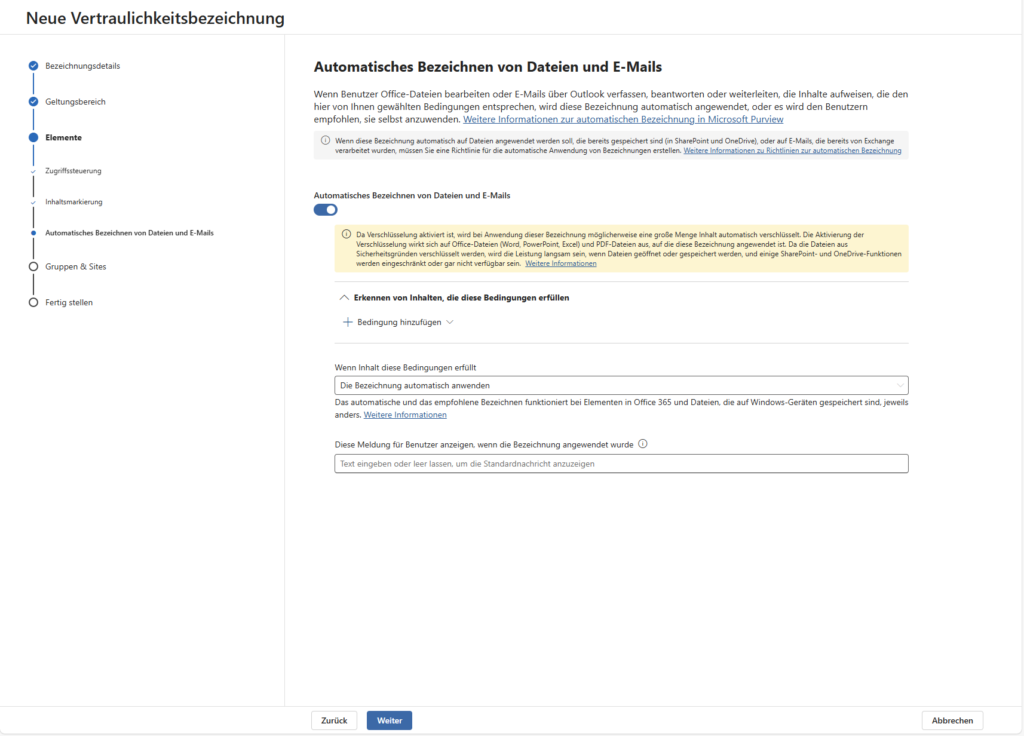
If you selected Elements, you can now configure the label’s Teeth. Here you decide what happens technically when a user clicks on the label.
A) Encryption
This is the strongest weapon of the Sensitivity Labels. You have two main strategies:
- Assign permissions now:
- Scenario: As an admin, you statically define who has access.
- Example: Label “Internal” = access for “All employees” (via dynamic Entra ID group). Label “HR Salary Data” = Access only for “Security Group HR”.
- Advantage: The user doesn’t have to think, the rules are fixed.
- Let users assign permissions:
- Scenario: Ad-hoc projects or e-mails to external parties.
- Function: When selecting the label, Office asks the creator, “Who can read this?” (similar to Do Not Forward in Outlook).
- Advantage: Maximum flexibility for business departments without IT having to build a new label for each project.
B) Content Marking
Markings make the protection status visually visible. You can force watermarks, headers, or footers .
- Practical tip: Less is more.
- A watermark (e.g., “Confidential” across the page) is effective, but it can make documents difficult to read. Choose subtle colors (light gray) and check readability.
- Headers/footers are often the better choice for everyday use, as they do not disturb the flow of reading, but still remain visible when printed.
5. Configure Label Policies (The “Who” and “Where”)
A label without a policy is invisible. You have painted the “sign”, but you have not yet hung it up. Label Policies control which users or groups are allowed to see which labels.
Go to Label policies and create a new policy. Here are the three most important adjustments for you as an admin:
A) Default Label
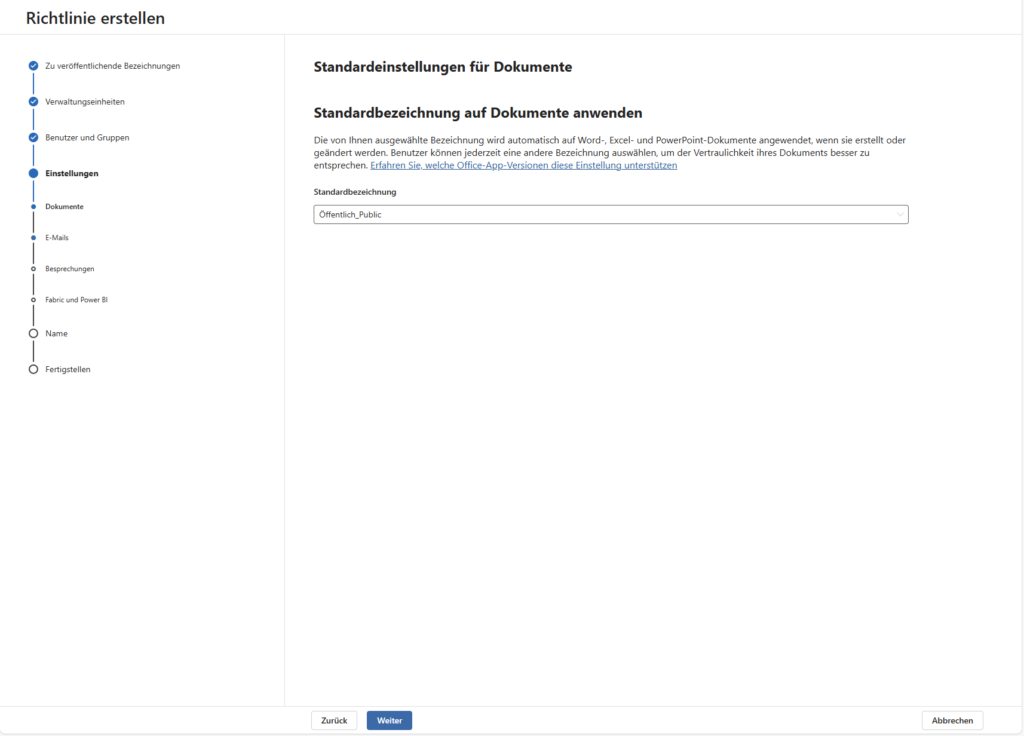
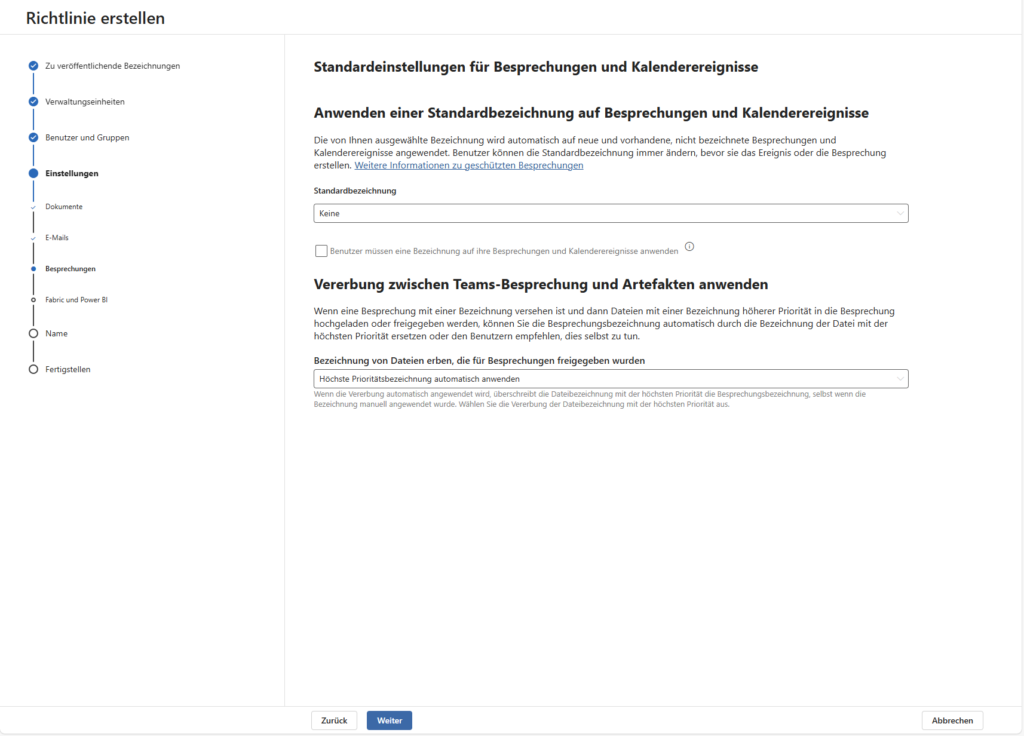
Here you can specify which label is automatically set when a user creates a new document or email.
- Best Practice: Many companies start with “General / Intern” as the default.
- Why? This ensures that no file remains unclassified (“naked”) without annoying the user with every email.
B) Mandatory Labeling (Erforderliche Bezeichnung)
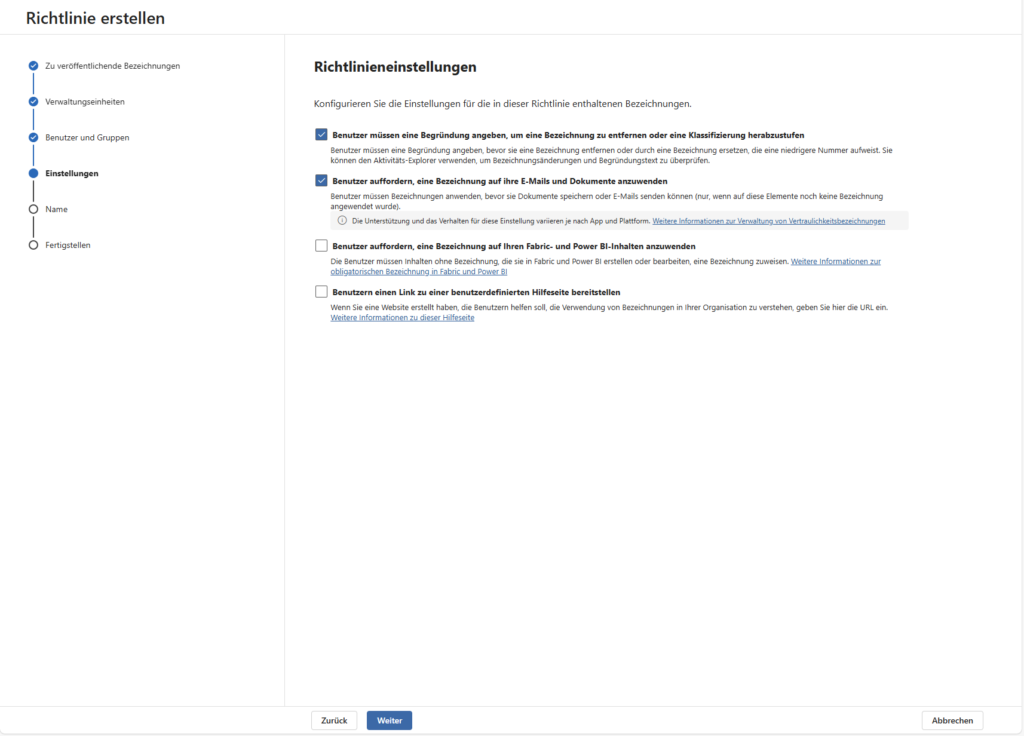
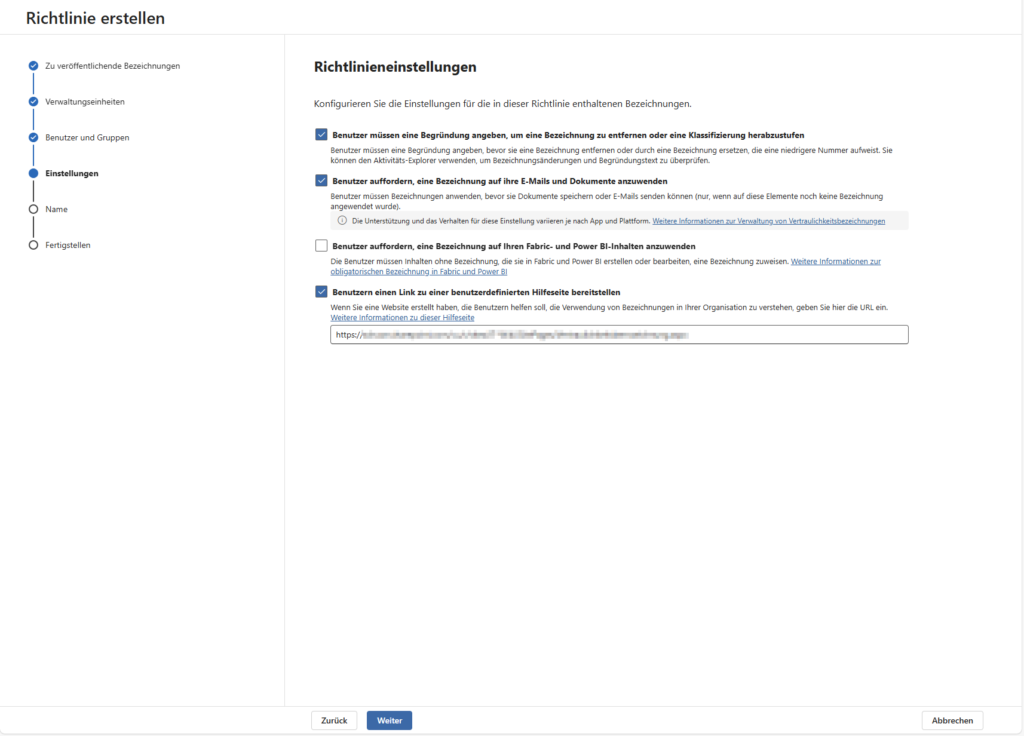
When you turn this on, you’re forcing the user to interact. He has to choose a label before he can save a document or send an email.
- When to use? This makes sense in highly regulated areas or when the “default label” strategy does not work.
- Caution: This can disrupt the workflow. Ideally, combine this with a Require justification to remove a label or lower its classification if users want to downgrade a label later.
C) Priority (IMPORTANT!)
The order of the labels in your list is not just cosmetic, it is logic.
- The rule: The label at the bottom of the list has the highest priority.
- The effect: Microsoft 365 uses this hierarchy to resolve conflicts.
- Example: If an email has an attachment labeled “Strictly Confidential” (high priority), but the email itself is set to “Public” (low priority), the client will suggest (depending on the setting) to promote the email. The system always protects in favor of the higher priority.
6. Deployment and testing
The most common mistake in the rollout is impatience. The Microsoft 365 compliance architecture is powerful, but not always fast.
- Pilot phase: Never immediately publish your first policy to “All Users”. Create an IT Pilot security group and assign the policy to it.
- The 24-hour buffer: Changes to label policies (create new, add labels, change settings) are not pushed in real time.
- It can take up to 24 hours for the labels to be visible in all Outlook clients, in Word Online, or on mobile devices.
- Admin tip: If a label doesn’t show up on the user, don’t start troubleshooting. Wait for the sync cycle first. Restarting the Office apps (or the “Reset Settings” button in the AIP Unified Labeling Client, if still in use) can sometimes speed up the process, but it is not a guarantee.
Monitoring & Reporting: Staying in Control
Trust is good, control is better. After the policies are rolled out, you need to know: Are they being used? Where is our sensitive data stored? For this purpose, Microsoft Purview offers two central tools in the area of “data classification”.
A) The Activity Explorer
Here you can see the dynamics in your tenant. Activity Explorer answers the question, “Who did what?”
- Which files have been relabeled?
- What files were downgraded (e.g., downgraded from Strictly Confidential to Public)?
- What files were printed or copied to USB sticks (in combination with Endpoint DLP)?
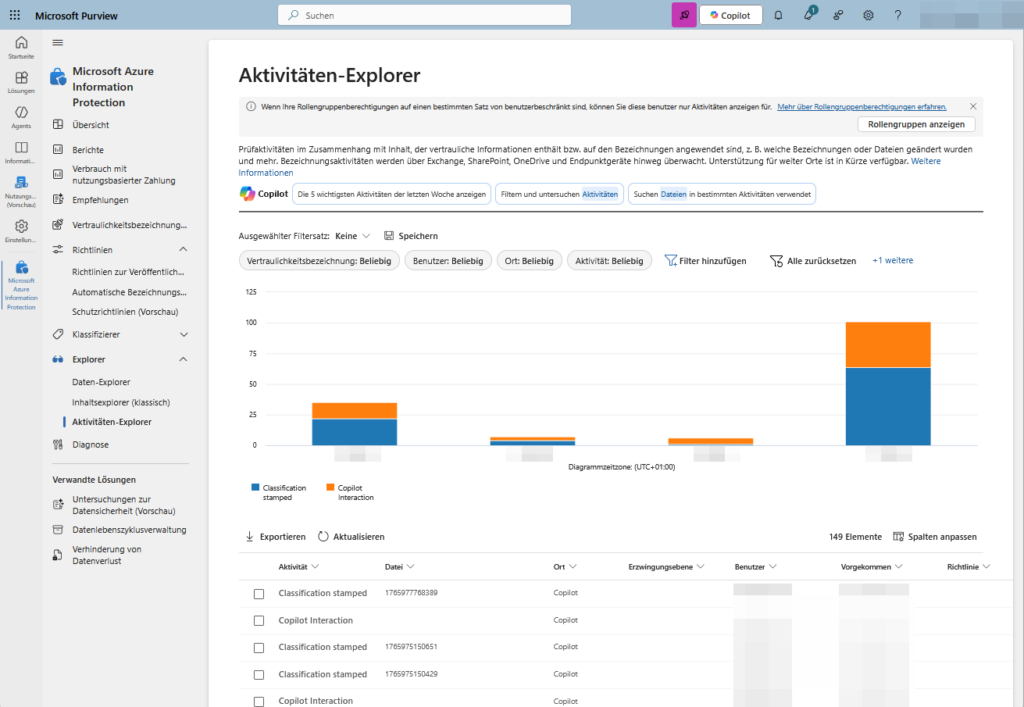
Admin tip: Use the “Activity” filter to search specifically for “Label changed “ or “Label removed”. These are often indicators of training needs or undesirable user behavior.
B) The Content Explorer
While the Activity Explorer shows actions, the Content Explorer shows the state. It answers the question: “Where is our data?”
You can navigate through SharePoint, OneDrive and Exchange here and see: “Aha, there are 50 files with credit card numbers in Mr. Müller’s OneDrive share.”
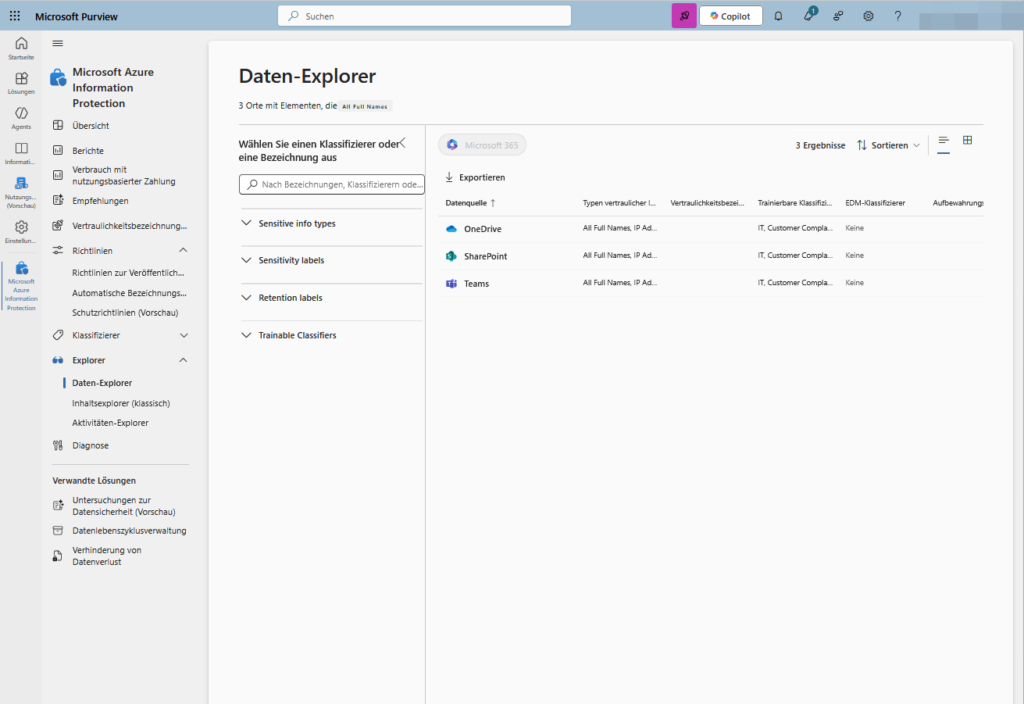
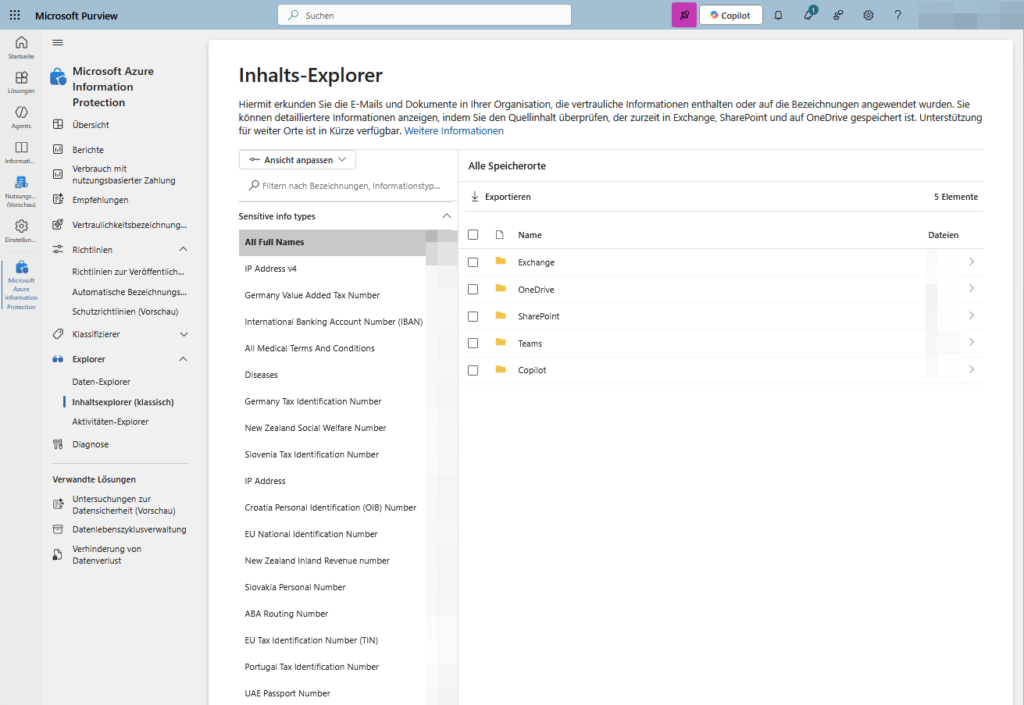
Important License Notice: As you may notice in the portal (and see in the screenshot above), full access to Content Explorer is often an E5 feature (or requires the Compliance add-on). With Business Premium, you often only see the top-level statistics, but you can’t “drill” deep into the file lists to check the exact content.
Deep Dive: Rights Management & Super User
… Expand details
Technically, Microsoft manages the cryptographic keys for your labels (RMS keys) unless you’re using complex niche solutions like DKE (Double Key Encryption). However, the biggest risk in everyday life is not the loss of the key at Microsoft, but the loss of access due to employee turnover.
The scenario: An employee is leaving the company. He created project files and labeled them with “Custom Access” or strictly restricted access to “Project Group A.” His account will be deleted. Years later, the legal department or an admin has to access these files. The problem: The encryption is still active, and the admin does not have permission to open the file. The file becomes a digital “paperweight”. Even as a Global Admin, you don’t have access to the encrypted content by default, only to the file (container).
The solution: The Azure Information Protection Super User feature To solve this problem, there is a kind of “master key” function for admins. This feature is disabled by default and must be explicitly enabled via PowerShell.
- Connect to the service: You need the AIPService PowerShell module.
Connect-AipService- Activate feature:
Enable-AipServiceSuperUserFeature- Add Super User: Now define dedicated admins or service accounts (e.g. for eDiscovery tools) who are allowed to decrypt everything.
Add-AipServiceSuperUser -EmailAddress "admin@dein-unternehmen.de"Conclusion: Without an active super-user feature, you risk being left in front of closed doors during offboarding processes or compliance investigations. Activate it in a controlled manner and monitor its use.
Automation: Client-Side vs. Service-Side Auto-Labeling
Manual classification is good, automation is better – but also more dangerous. Microsoft Purview offers two fundamentally different ways to set labels without user interaction. As an IT admin, you need to know the difference to avoid performance issues and correctly assess licensing.


License warning in advance: While manual labels are part of Microsoft 365 Business Premium , automatic classification (based on content) typically requires an E5 license or the Compliance Add-on. If you’re using Business Premium, the following points are more to help you understand what would be possible if you upgraded.
1. Client-Side Auto-Labeling (The “Accessibility”)
This happens directly in the app (Word, Excel, Outlook) on the user’s device.
- How it works: As soon as a user types a credit card number or works on a document, the local client analyzes the content against the configured Sensitive Information Types (SITs).
- The effect: The user immediately receives a tooltip (“We have found sensitive data, please use the ‘Confidential’ label”) or the label is automatically set when saving – depending on the policy.
- Advantage: Immediate feedback and learning effect for the user (“Education in the flow of work”).
2. Service-Side Auto-Labeling (The “Background Scanner”)
This is the more powerful weapon that runs completely without user interaction at the server level (SharePoint, OneDrive, Exchange).
- The process: Microsoft’s cloud services scan data at rest or emails in transit. If the scanner finds suitable patterns, the file is labeled and encrypted in the background.
- Safety First (Simulation Mode): You can (and should never “arm” a service-side policy immediately. Purview almost forces you to use the simulation mode first.
- The policy runs for up to 24 hours in test mode.
- You’ll get a report: “I would have marked 5,000 documents as ‘Strictly Confidential.'”
- Only if this report does not show any false positives, you activate the policy.
Excursus: What does automation respond to? (The Detection Methods)
For automation to take effect, the system must know what to look for. Here, Purview offers three levels of intelligence:
A) Sensitive Information Types (SITs)
This is the standard. Microsoft provides hundreds of templates for pattern recognition (RegEx): credit card numbers, ID numbers, tax IDs. You can also define your own patterns here.
B) Trainable classifiers
This is where machine learning comes into play. Patterns such as “source code”, “workplace harassment” or “tax documents” cannot be easily found via RegEx. These classifiers look at the semantic context of the document.
- Note: As you can see in the screenshot, this is a clear E5 feature.
C) EDM classifier (Exact Data Match)
For absolute precision. If you want to know exactly whether a customer number belongs to your customer base (and is not just some 10-digit number), you upload hash values of your database. Purview then compares exactly against this data.
Troubleshooting & Diagnostics: When things get stuck
Despite the best planning, it happens: A user does not see his label, or the encryption. Microsoft Purview provides a Diagnostics pane for this purpose.
Here you can have typical scenarios checked directly without having to pore over PowerShell logs.
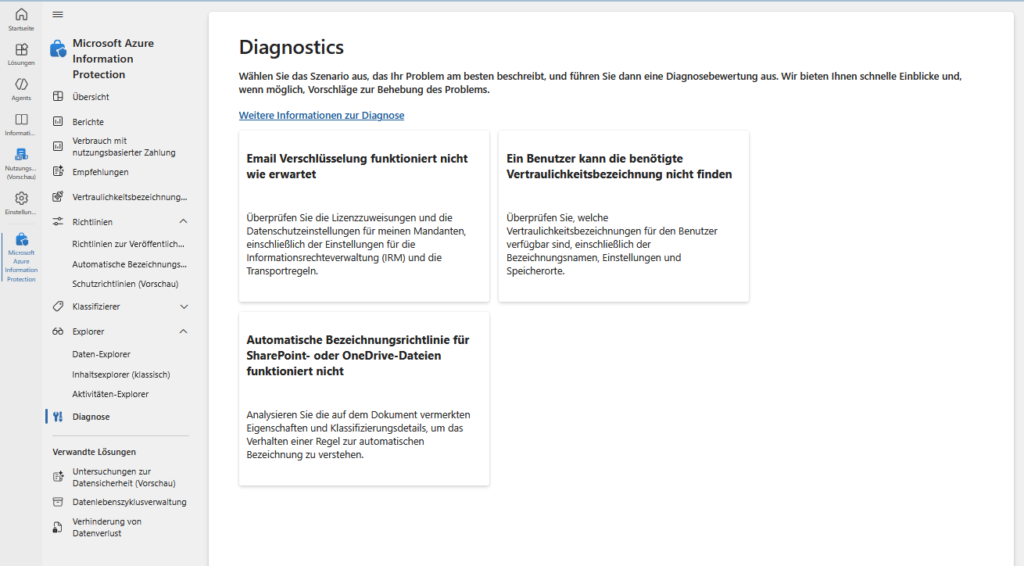
Common scenarios for the admin:
- A user can’t find the name they need:
- Cause: Most of the time it is due to the label policy. Is the user really in the security group to which the policy has been assigned?
- Check: Use the diagnostic tool (see screenshot, right box), enter the username, and the system will check which policies effectively apply to this user.
- Sync Delay:
- Remember the “24-hour rule”. If you have just added a user to the group, it may take some time. Restarting the Office apps often helps, but does not force an immediate sync from the server.
- Encryption issues:
- If external users are having problems, check the Activity Explorer to see if access was denied or if the problem is with the other party’s identity provider.
– Sensitivity labels as a strategic foundation
Sensitivity labels are no longer an optional “nice-to-have”, but the foundation of a modern Zero Trust architecture. The old approach of “we build a high wall around our network” no longer works in times of home office and cloud collaboration.
The target state is clear: sensitive data protects itself – through encrypted metadata that travels with the file. But the reality in many companies often shows a gap between aspiration and implementation. Labels are often only introduced rudimentarily because the complexity of encryption (Azure RMS) and taxonomy is shied away.
However, if you invest the time in proper planning (crawl-walk-run approach), you will benefit enormously:
- Compliance without additional tools: GDPR requirements and ISO 27001 specifications for data classification are often supported “out of the box”.
- Mitigating shadow IT: If files are encrypted, it doesn’t matter (almost) whether they accidentally end up in a private Dropbox – they remain unreadable data garbage for third parties.
- Transparency: Data protection becomes measurable and comprehensible.
Outlook: The role of AI and data map
The journey doesn’t end with Office documents. Microsoft is massively expanding the integration:
- Microsoft 365 Copilot: This is currently the most important driver. Copilot respects sensitivity labels and the associated rights of use.
- The risk: Without labels, Copilot can unintentionally disclose or aggregate sensitive data (e.g., salary tables) that the user has access to in summaries or responses in an insecure context (e.g., chat on the web).
- Protection: Labels prevent AI from including sensitive content (e.g., from payrolls) in summaries for unauthorized users. Without clean labels, the use of AI becomes an incalculable risk.
- Structured Data: In the future, labels will increasingly be extended to structured data via the Microsoft Purview Data Map . So the label concept is growing beyond Word and Excel towards SQL databases, Azure Blob Storage, and even AWS S3 buckets.
Those who lay the foundations and train their employees today not only build protective mechanisms, but also prepare their company for an automated, AI-supported future.
Status: December 2025
further links
| General Introduction: Understanding sensitivity labels, scope, and capabilities. | https://learn.microsoft.com/de-de/purview/sensitivity-labels |
| Create labels: Step-by-step instructions for creating and publishing labels. | https://learn.microsoft.com/de-de/purview/create-sensitivity-labels |
| Encryption (Azure RMS): Technical deep-dive of how encryption and rights assignment works. | https://learn.microsoft.com/de-de/purview/encryption-sensitivity-labels |
| Container-level protection: Enable labels for Microsoft Teams, Microsoft 365 Groups, and SharePoint sites. | https://learn.microsoft.com/de-de/purview/sensitivity-labels-teams-groups-sites |
| Enable co-authoring: Prerequisite for co-editing encrypted files. | https://learn.microsoft.com/de-de/purview/sensitivity-labels-coauthoring |
| Licensing guide: Excel/PDF matrix showing which functions (e.g. auto-labeling) require which license. | https://learn.microsoft.com/de-de/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance |
| Client integration: Comparison between the built-in labeling client (built-in) and the old AIP client. | https://learn.microsoft.com/de-de/purview/sensitivity-labels-office-apps |
| Super User Feature: Activation of the “master key” for admins for data recovery. | https://learn.microsoft.com/de-de/purview/encryption-super-users |
| Service-side: Configure auto-labeling for data-at-rest (SharePoint/OneDrive). | https://learn.microsoft.com/de-de/purview/apply-sensitivity-label-automatically |
| Auto-labeling (client-side): Recommended or enforced labels directly in Office apps. | https://learn.microsoft.com/de-de/purview/apply-sensitivity-label-client |
| Activity Explorer: Monitor label activity, changes, and downgrades. | https://learn.microsoft.com/de-de/purview/data-classification-activity-explorer |
| Content Explorer: Overview of where which classified data is stored in the tenant (requires special rights). | https://learn.microsoft.com/de-de/purview/data-classification-content-explorer |
| Sensitive Information Types (SITs): List of standard patterns (credit cards, ID cards) for detection. | https://learn.microsoft.com/de-de/purview/sensitive-information-type-learn-about |
| External collaboration: Best practices for encrypted documents with guests. | https://learn.microsoft.com/de-de/purview/secure-external-collaboration |
| Microsoft 365 Copilot & Security: How labels prevent AI from exposing too much data. | https://learn.microsoft.com/de-de/copilot/microsoft-365/microsoft-365-copilot-privacy |






Be the first to comment