In modern IT security, identity is the new firewall. For administrators, this means that protecting user accounts in Microsoft Entra ID (formerly Azure AD) is a top priority. But default settings are often not enough.
In this article, we’ll take a look at the native security features of Entra ID, the authentication methods – password protection, that effectively minimize attack vectors like password spraying and brute force.
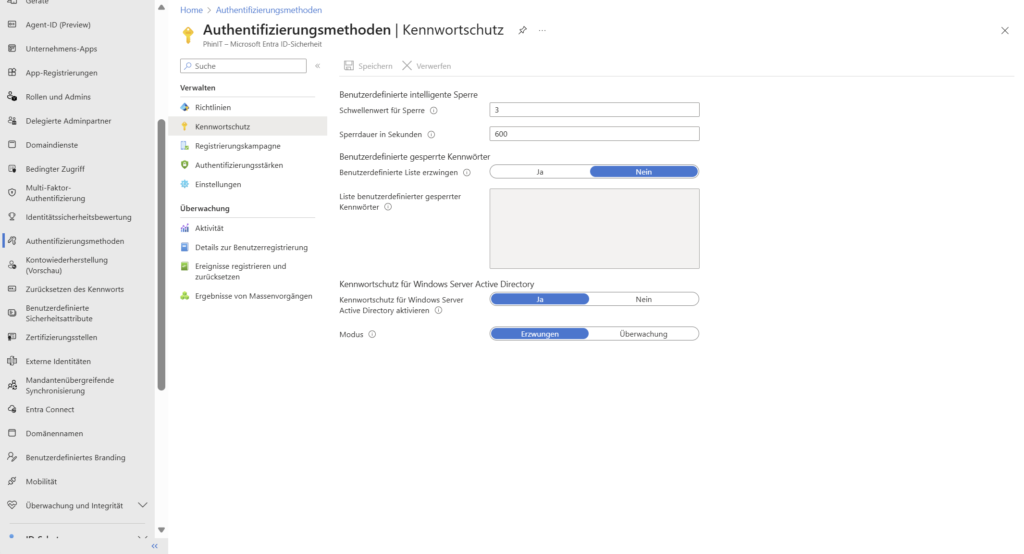
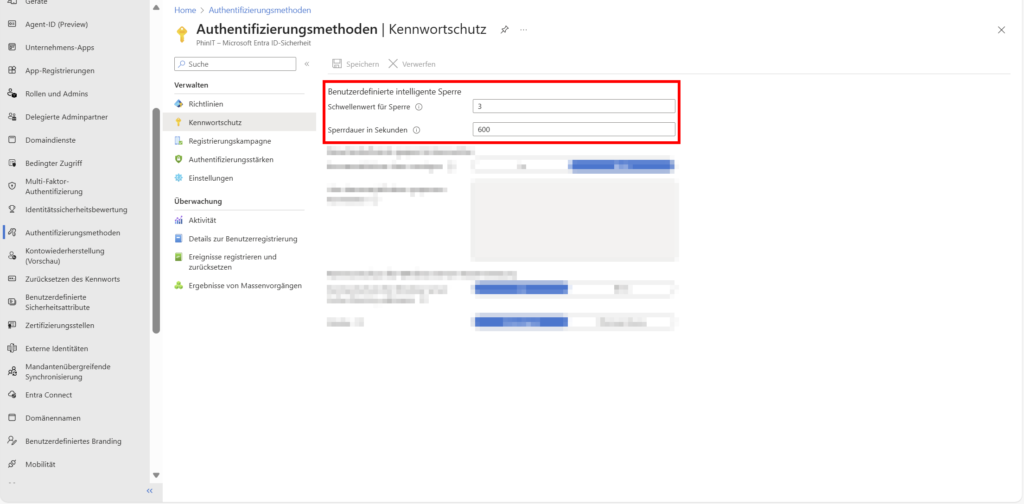
1. Password Protection | Account lockout, threshold, and lockout duration
In contrast to classic Active Directory account lockout, Smart Lockout acts more intelligently in the cloud. It uses cloud intelligence to distinguish between login attempts by a legitimate user and those of an attacker.
- How it works: The system specifically locks out the attacker (based on IP/location) while still allowing the real user to log in. This prevents denial-of-service (DoS) scenarios at the user level.
- Configuration: The default value is 10 failed attempts with a 60-second lock. With an Entra ID P1 license , you can adjust these thresholds.
Hybrid tip: Sets the threshold in Entra ID lower than in on-premises AD to prevent cloud attacks from locking out the on-premises account.
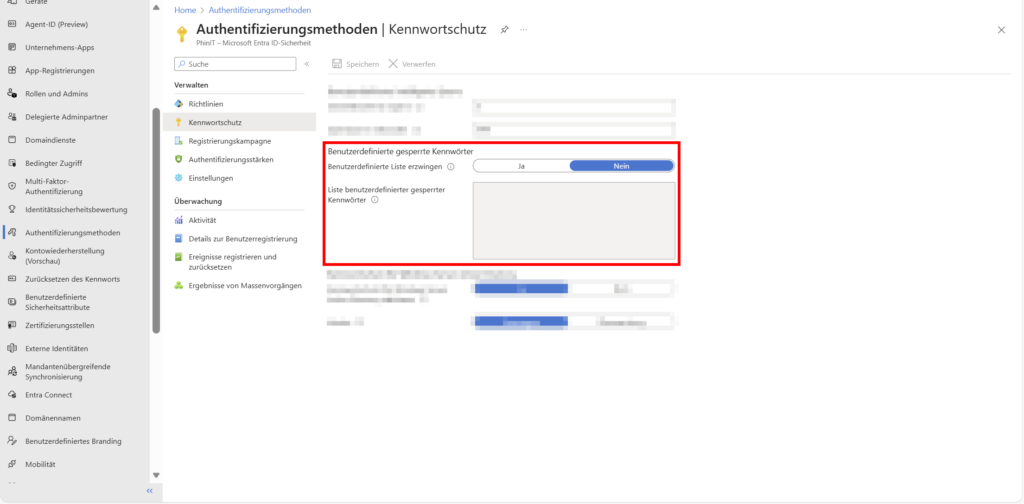
2. Custom locked passwords
Entra ID already has a Global Banned Password List, which blocks trivial terms such as “Password123”. For targeted protection, you can also define a custom list (requires Entra ID P1).
- Use Case: Blocks company-specific terms such as the company name, local sports clubs or “Standort2025”.
- Normalization: The algorithm is smart – if you block “company”, “F1rma!” or “fiRma” will also be blocked.
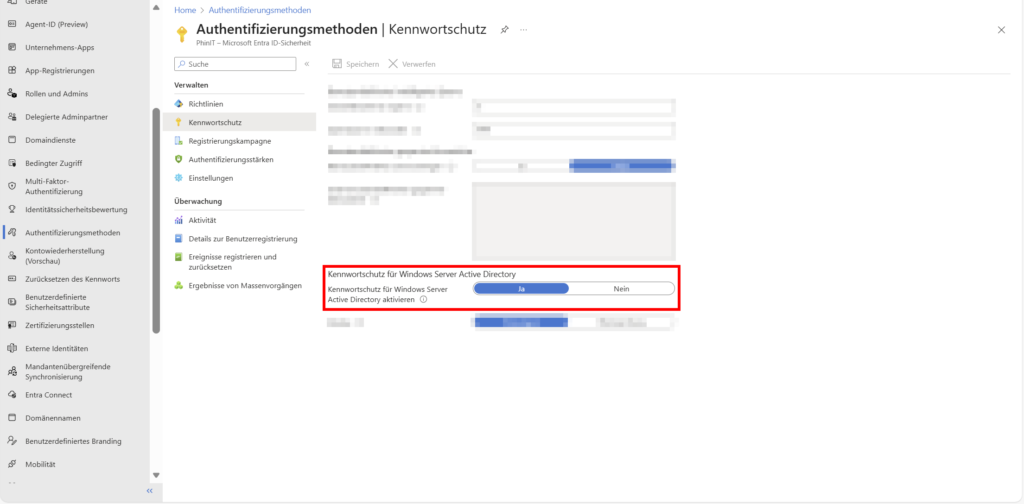
3. Password protection for Windows Server Active Directory
Many attacks still take place on-premises. With the Microsoft Entra Password Protection Proxy and the DC Agent, you can extend the cloud rules (see point 2) to your local domain controllers.
- Advantage: Users can no longer set a weak password – neither on the Windows login screen nor via admin reset. This raises the security level of the entire hybrid environment to cloud standard.
Result
The native features of Microsoft Entra ID provide a powerful toolbox. The combination of Smart Lockout, Banned Passwords and Active Directory CLoud LAPS forms the basic line of defense. If you want to go one step further, plan the path towards passwordless. It’s important not to look at these features in isolation, but as part of a Zero Trust strategy.
⚠️ Important note on password guidelines (Update 2024/2025)
Contrary to earlier recommendations, current security standards (BSI Grundschutz, NIST 800-63B) now advise against forcing users to change passwords regularly (e.g. every 90 days).
The reason: Forced changes lead to weak patterns (“Summer2024!”, “Summer2025!”).
- Best Practice: Relies on strong, durable passwords in combination with MFA and only exchanges passwords if there is a concrete suspicion of compromise (Identity Protection Risk Events).
Important note
It’s important to note that new policies and settings in Microsoft Entra ID don’t take effect until you change your password or create new user accounts. Therefore, it is recommended to encourage regular password changes and educate users about the importance of strong passwords.
FAQs for Admins
What is the difference between Smart Lockout and AD Lockout? Smart Lockout (Cloud) uses AI to block attacker IPs, while the real user often still has access. The classic AD lockout usually locks the account globally.
What license do I need for Custom Banned Passwords? For the global list, the free version is sufficient. To block your own terms (company name, etc.), Entra ID P1 (or Business Premium) is required.
How do I enable on-premises password protection? To do this, the Microsoft Entra Password Protection Proxy Service and the DC Agent must be installed on the local servers. A P1 license is required.
Does “Password Expiration” still make sense? No. Modern standards (NIST/BSI) and Microsoft recommend setting passwords to “Does not expire” and using MFA and Leaked Credential Detection instead.
What are the benefits of Password Writeback? It allows hybrid users to change their password in the M365 portal, with the change being instantly replicated to the local AD. prerequisite for functioning SSPR in hybrid worlds.





Be the first to comment