In modern identity management, multi-factor authentication (MFA) is the gold standard. But attackers don’t sleep: Techniques such as MFA fatigue aim to bombard users with push notifications until they agree in annoyance.
Microsoft Entra ID offers specific toggles in the admin center to prevent this from happening. In this article, we’ll show you how to correctly set the number matching, application name , and geographic location sliders in the Microsoft Authenticator policy.
The way to the settings
Before we get into the details, here’s the configuration in the Microsoft Entra admin center:Authentifizierungsmethoden | Richtlinien > Richtlinie “Microsoft Authenticator” select > Tab “Konfigurieren".
🆕 Update: Since the cloud is constantly changing, we are constantly reviewing this guide. Nevertheless, a look at the official Microsoft documentation is mandatory to stay up to date with critical changes.
📅 Booth | 22.12.2025

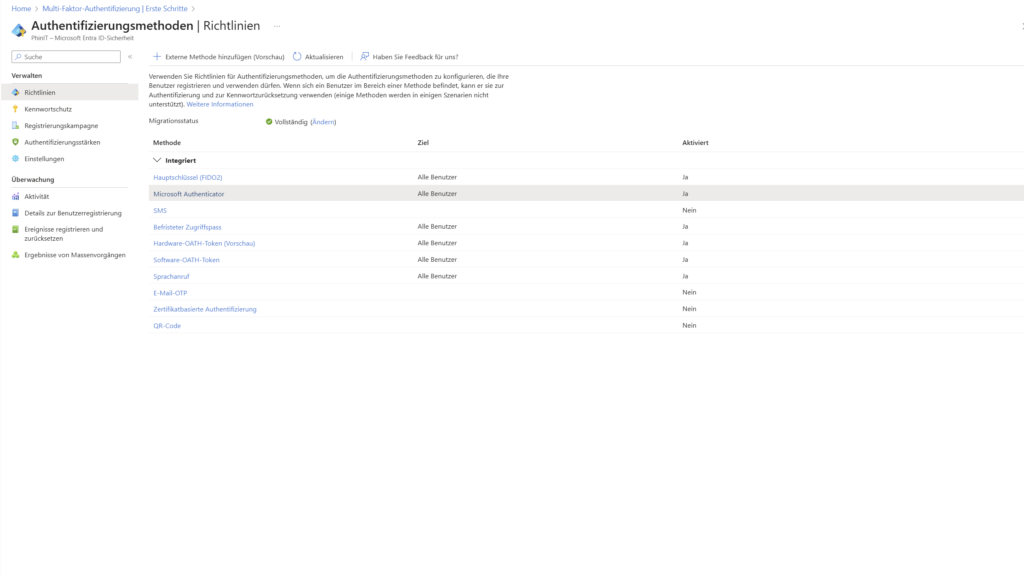
Standard: Number Matching
Number matching is no longer an optional feature, but was largely enforced as the standard by Microsoft in May 2023. Still, it’s important to understand why this happened.
In your admin center, you’ll see that the status is set to “Enabled” under “Require number matching for push notifications.”
- The problem (MFA fatigue): In the past, a simple tap on “Approve” was enough. Attackers took advantage of this by sending hundreds of requests at night in the hope that the victim would inadvertently confirm.
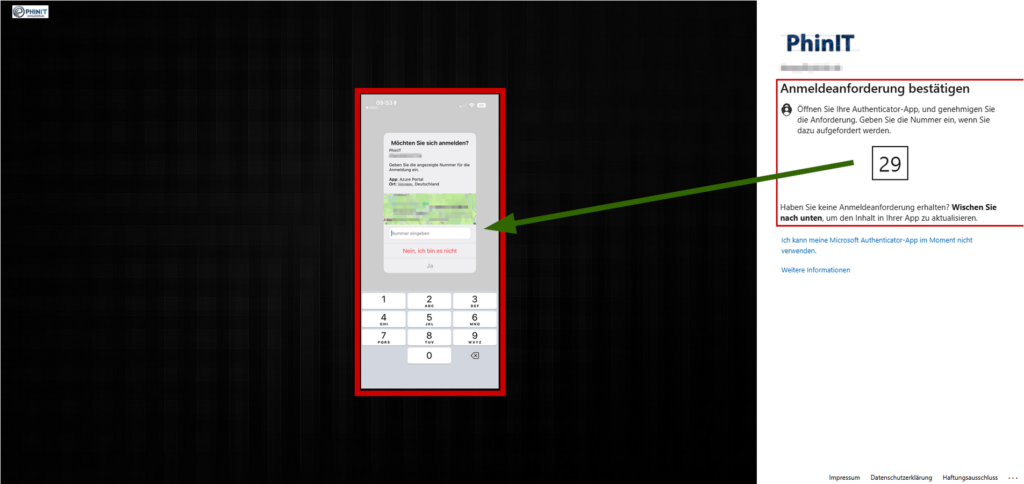
- The solution: The user must type a two-digit number displayed on the login screen into the app.
- The effect: This stops automated attacks immediately, as the attacker cannot see the number on the victim’s screen. An “accidental” confirmation is technically impossible.
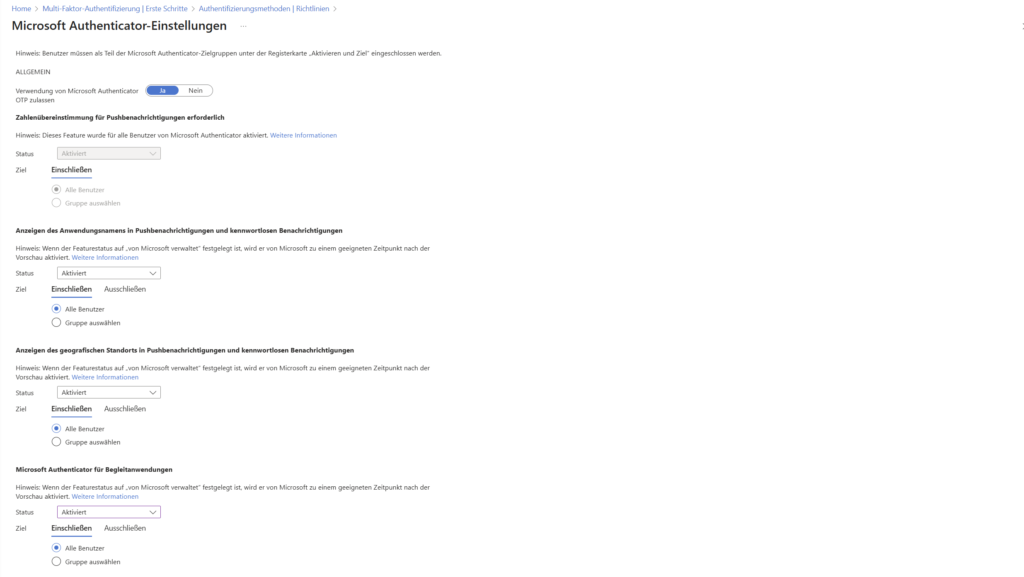
Show application and location in notifications
While the number match is mandatory, the context information is often still optional or is set to “Managed by Microsoft”. To maximize transparency for your users, you should actively engage them.
A) Displaying the Application Name in Push Notifications
- Recommended setting:
- Status: Enabled
- Target: All users
- The effect: Instead of a generic request, the user sees: “Login to: Microsoft Teams”.
- Why important: If a user is just opening Outlook but receives a request for “Azure Portal”, they will immediately recognize the discrepancy.
B) Displaying geographic location in push notifications
- Recommended setting:
- Status: Enabled
- Target: All users
- The effect: The app shows a map or the location of the requesting IP address (e.g. “Berlin, Germany”).
- Admin Note: This is based on IP geolocation. It is not GPS-accurate, but it is quite sufficient to detect attacks from foreign countries.
Other important settings in check
Allow the use of Microsoft Authenticator OTP
- Recommendation: Yes
- Reason: OTP (One-Time Password / 6-digit code) is the lifeline when the device is offline (e.g. on the plane or in the server room without reception). If you deactivate this, you lock out users in dead zones.
Microsoft Authenticator for Companion Applications
- Status: Managed by Microsoft
- Explanation: This setting controls integration with wearables (smartwatches). Since Microsoft has largely discontinued support for the Apple Watch app (watchOS), the “Managed by Microsoft” setting is the safest choice here. You don’t have to change anything manually here.
The premier class: Passwordless login
All of the above settings also apply to Passwordless mode. This is the most effective protection against phishing, as the classic password is no longer transmitted at all. We distinguish between two methods within the Microsoft Authenticator app:
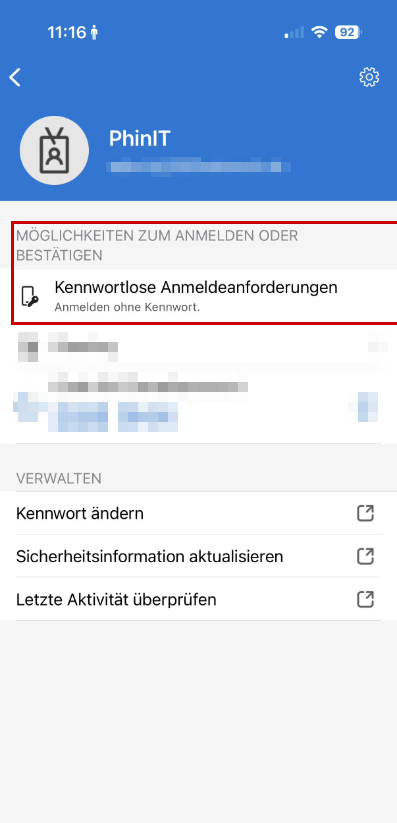
1. Phone Sign-in (notification)
To use this mode, make sure that the authentication mode is set to “Any” instead of “Push” in the “Activate and Target” tab.
- The process: The user enters their username, confirms the number displayed in the app and verifies themselves via biometrics (FaceID/fingerprint).
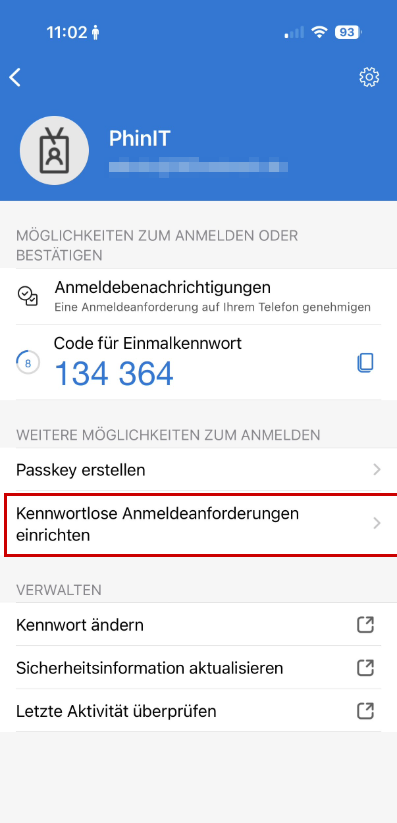

2. Passkeys (The New Standard)
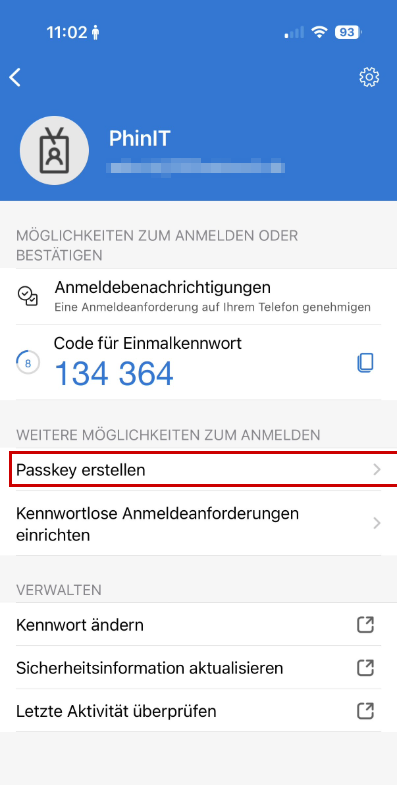
Passkeys are the next evolutionary step (FIDO2). They are device-bound and offer the highest level of security.
- The furnishings: For this purpose, the FIDO2 security key method must often also be activated in the admin center and released for the Authenticator app.
- The advantage: A passkey works like a digital master key that is securely stored on the smartphone. It is phishing-resistant because it only connects to the real, original website. The login is done at lightning speed via biometrics – without having to compare a number.
Conclusion | Not all MFA is the same
Even though Microsoft has massively increased the technical hurdle for attackers with the now enforced number matching , the “human” factor remains the weakest link. A user who blindly types in numbers is hardly safer than one who blindly presses “Approve”.
The responsibility for transparency therefore lies with you. Only if the employee understands what he is releasing can he act as an effective “human firewall”.
Tip: Communication is everything (change management)
Don’t turn on these features “secretly” overnight. Users often react unsettled when their login app suddenly looks different (“Will I be hacked? Why is there suddenly a place?”).
Send a short info (Teams/Mail) before the changeover:
“Dear colleagues, in order to protect your accounts even better from attacks, we are updating the Microsoft Authenticator. From [date] onwards, you will also be able to see which app is requesting access and from which location the request is coming when you log in. This helps you to immediately distinguish real requests from fraudulent ones. If you see a request that you did not trigger yourself: Please decline and inform IT!”
The result
With these adjustments, you can turn cryptic login requests into clear, understandable decisions. You drastically minimize the risk of human error and give your users the tool to actively defend their own identity.





Be the first to comment