Windows Server is at the heart and often the crown jewel of your enterprise infrastructure. However, its central role makes it a preferred target. Hardening is not just a checklist, it’s a strategic necessity. It means systematically decimating the attack surface and configuring security mechanisms in such a way that even complex attacks come to nothing.

This article provides you as an IT administrator with the blueprint for Windows Server Hardening that can withstand the current threats.
Our goal: A robust server that not only protects, but builds trust.
Hardening: Principles & Mindset
Before technical measures such as firewall rules or GPOs take effect, the underlying security strategy must be clear.
Hardening is an architectural decision based on three fundamental imperatives.
1.1. The Least Privilege Principle (PoLP)
The PoLP is the central pillar of the security architecture. It states that each subject (user account, service account, process) should only receive the minimum necessary access rights (permissions) and the minimum necessary time (just-in-time administration) to fulfill its specific task.
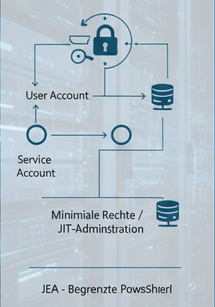
To implement this , managed service accounts (MSAs) or group managed service accounts (gMSAs) should be used instead of traditional user accounts for services.
These enable automatic password management by Active Directory and are limited to specific servers, which reduces the risk of pass-the-hash attacks.
Check the Service SID (S-1-5-80-…) and use it to assign permissions to services directly and in isolation, instead of including the entire service account in local groups. Similarly, Just Enough Administration (JEA) must be used in PowerShell to allow administrative accounts to run only a limited list of cmdlets.
1.2. Attack Surface Reduction
Every feature, every open port, and every installed component is a potential vector for an attacker. Hardening aims to radically reduce this attack surface .
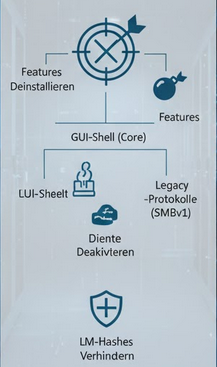
This requires uninstalling unneeded Windows features, especially graphical user interface components (Server-Gui-Shell) for core installations.
Another focus is on disabling legacy protocols such as SMBv1 or the Link-Layer Topology Discovery (LLTD) protocol driver.
Likewise, services that are not needed (e.g. fax, Bluetooth) must be stopped and deactivated.
A critical step is to disable the storage of LAN Manager hashes by setting the GPO “Network Security: LAN Manager Authentication Level” to at least “Send NTLMv2 responses only. Deny LM and NTLM” (Level 5).
1.3. Defense-in-Depth (Schutz in der Tiefe)
This principle recognizes that no single security mechanism is perfect . It requires the implementation of multiple, overlapping controls that function independently of each other, so that the attacker must overcome each of these layers individually.
The controls must be layered:
- Network: Host-based firewall (Windows Defender Firewall), network segmentation (VLANs, microsegmentation).
- Host/Operating System: AppLocker/WDAC (Application Whitelisting), Credential Guard, Endpoint Detection and Response (EDR) solution, advanced audit policy.
- Data/Application: NTFS permissions (ACLs), encryption (BitLocker), database access control.
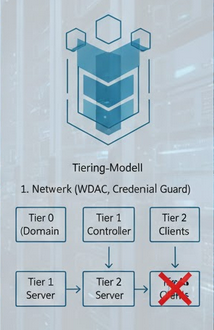
In addition, the tiering model (isolation) must be implemented: The Tier 0, Tier 1, Tier 2 model for Active Directory logically separates the most critical assets (Tier 0: domain controllers, admin workstations) from less critical environments to minimize the risk of lateral movement after a compromise.

1. Preparation: Inventory and Radical Cleanup
The first and crucial step in server hardening is inventory, a complete and honest inventory of the environment.
You need to know exactly what is running on the server in order to be able to precisely identify and minimize the attack surface . This process includes the critical question:
- What’s really going on? (Required services and applications that are currently in use)
- What is just historical ballast? (Deprecated services, software that is no longer needed, open ports, test installations or old configurations)
A. Analysis of Installed Components and Processes

Use PowerShell for a fast, accurate, and comprehensive overview of all installed components and their status.
- Roles and Features:
Check which components are installed and can potentially be removed.Liste aller installierten Rollen und Features (InstallState = Installed) Get-WindowsFeature | Where-Object {$_.InstallState -eq "Installed"} | Select-Object Name,DisplayName - Ongoing services:
Determine which services start automatically or are active. Every running service is a potential point of attack.Liste aller Dienste mit StartType 'Automatic' und Status 'Running' Get-Service | Where-Object {$_.StartType -eq "Automatic" -and $_.Status -eq "Running"} - Open ports:
Take an inventory of the active TCP and UDP listeners. These define your current network attack surface.Zeigt alle aktiven TCP-Listener (mit Prozessinformationen) Get-NetTCPConnection -State Listen | Select-Object LocalAddress, LocalPort, OwningProcess
Specialized tools (e.g easyADReport . or easyConnections) can be used for an in-depth inventory of the Active Directory status.
B. Decommissioning and Consistent Removal

Mercilessly remove all roles, features and unnecessary components that do not directly belong to the defined server role (e.g. domain controller, web server).
Remove features
Focus on removing GUI components for core installations (Server-Gui-Shell), deprecated services (print or fax services), and legacy communications. Example: Removing an unneeded feature (adjust!). Important: The -Remove parameter removes the source files for later installation.
Uninstall-WindowsFeature -Name <FeatureName> -Remove| GUI shell / desktop experience | Removing the graphical user interface is the most important hardening measure on a backend server. It drastically reduces the attack surface. Uninstall-WindowsFeature -Name Server-Gui-Shell, Server-Gui-Mgmt-Infra -Remove |
| Windows Search | Search indexing consumes resources and is unnecessary on dedicated servers (except file servers). Uninstall-WindowsFeature -Name Windows-Search -Remove |
| XPS Viewer / XPS Services | Document viewing and services. These components are not required on most backend servers. Uninstall-WindowsFeature -Name XPS-Viewer -Remove |
| Client for NFS | Services for the Network File System. Only necessary if the server needs to access UNIX/Linux file shares as a client. Uninstall-WindowsFeature -Name NFS-Client -Remove |
| Wireless LAN Service | Wireless network support is irrelevant on physical servers in the data center or virtual machines. Uninstall-WindowsFeature -Name Wireless-Networking -Remove |
| BranchCache | A feature for WAN optimization. Often superfluous on central servers or in environments with defined WAN accelerators. Uninstall-WindowsFeature -Name BranchCache -Remove |
| Internet Explorer (Capability) | A legacy component. Should be removed for security reasons when no critical application needs it. dism /online /Remove-Capability /CapabilityName:Browser.InternetExplorer~~~~0.0.11.0 |
| Media Base | Includes basic multimedia features. Almost always unnecessary on dedicated servers. Uninstall-WindowsFeature -Name Media-Foundation -Remove |
| PowerShell 2.0 Engine | An outdated version of the PowerShell engine. Should be removed as it may have security vulnerabilities. Uninstall-WindowsFeature -Name PowerShell-V2 -Remove |
Disable critical services
Services that are not needed must not only be stopped, but their startup type must Disabled be set to prevent a restart. Example: Deactivating the fax service
Set-Service -Name Fax -StartupType Disabled| Print Queue (Spooler) | Spooler | Disable if the server is not processing print jobs. |
| Remote registration | RemoteRegistry | Disable to prevent unauthorized remote access to the registry. |
| SSDP Search | SSDPSRV | Disable. For searching for UPnP devices, which is usually unnecessary on servers. |
| Sensor Data Service | SensorDataService | Disable. Collects data from sensors, irrelevant to most servers. |
| Diagnostic Policy Service | DPS | Disable. For detecting, remediating, and logging system issues. Can be disabled in case of strict hardening (if monitoring is done externally). |
| IP Auxiliary Service | iphlpsvc | Disable if no transition technologies (such as Teredo, 6to4) or advanced network services are needed. |
| Automatic Wi-Fi configuration | WlanSvc | Disable, as this is irrelevant for stationary servers. |
| Workstation service | LanmanWorkstation | Caution! This service is necessary to connect to SMB shares. It should only be disabled if the server never accesses external shares (for example, on an isolated domain controller). |
| Windows Connect Now Configuration Registration Service | Wcncsvc | Disable. Used for Wi-Fi configurations that are unnecessary on servers. |
| Bluetooth Support Service | bthserv | Disable. Bluetooth is unnecessary on servers. |
| GameInput Service | GameInputSvc | Disable. A service for game controller input; irrelevant. |
| Touch keyboard and handwriting service | TabletInputService | Disable. Relevant only for touch or pen input. |
C. Audit checkpoints for a minimum attack surface

Check and disable the following critical vectors immediately if they are not absolutely necessary:
| SMBv1 | Must be disabled as it is a major vector for ransomware (e.g., WannaCry) and man-in-the-middle attacks. | PowerShell: Set-SmbServerConfiguration -EnableSMB1Protocol $falseGPO (Client): Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters" -Name "EnableSecuritySignature" -Value 1 -Type DWORD |
| Telnet/FTP Server | These unencrypted protocols are outdated and need to be uninstalled. Allow only secured alternatives (SSH/SFTP, WinRM). | PowerShell (uninstall): Uninstall-WindowsFeature -Name Telnet-Server, Web-Server, Web-Ftp-Server -Remove |
| Windows Remote Management (WinRM) | Use only when necessary and secure via HTTPS (port 5986) if possible. Access must be strictly limited to administrators and defined source IPs. | GPO (access): Create a Windows Firewall rule for WinRM (port 5985/5986) that only allows defined IP addresses as a source. |
| Legacy Authentication (LM/NTLMv1) | The storage of LAN Manager (LM) hashes must be disabled as they are extremely easy to crack. NTLMv1 should also be disabled. | GPO (LM): Computer Configuration > Guidelines > Windows Settings > Security settings > Local Policies > Security options > Network Security: Set LM Authentication Level to Level 5 (Send NTLMv2 Response Only, Deny LM & NTLM). |
| NTLMv1 Limitation | Prevent the use of older, insecure NTLMv1 protocols. | GPO (NTLMv1): Computer Configuration > Guidelines > Windows Settings > Security settings > Local Policies > Security options > Network Security: NTLM Restriction: Set NTLM check for incoming traffic to Deny All Accounts . |
| LLMNR and NBT-NS (NetBIOS) | Link-Local Multicast Name Resolution and NetBIOS Name Service. These protocols are vulnerable to responder attacks (name resolution poofing) and should be disabled in domain environments. | GPO: Computer Configuration > Administrative Templates > Network > DNS Client > Disable Multicast Name Resolution Protocol (LLMNR) Set to Enabled . Network adapters: Disable NetBIOS (TCP/IP settings). |
| IPv6 (deactivation) | Only deactivate it if it is definitely not used. In general, Microsoft recommends keeping IPv6, but in highly hardened environments with no clear usage, it can be an attack surface. | PowerShell (deactivation only via registry): Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters" -Name "DisabledComponents" -Value 0xff -Type DWORD |
2. Network and Protocol Hardening
The network is the primary and most widely used attack vector . Due to the large number of devices, services and open connection points, it offers attackers the largest surface area to penetrate systems or intercept sensitive data.
Here, the entire strategy revolves around rigorously closing insecure communication paths, segmenting traffic, and enforcing and encrypting secure communications. This includes:
A. Banish Insecure Legacy Protocols

Disable protocols with known, critical vulnerabilities. The priority is to remove protocols that are abused for lateral movement and ransomware .
| Hardening Test Point | Technical Imperative | PowerShell / GPO measure |
| Enforce LDAP Signing & Channel Binding | Must be enabled in Active Directory environments to prevent MITM attacks in LDAP communication. | GPO (DC): Domain Controller: Set LDAP server signing requests to Require Signature . |
| Disable LLMNR and NBT-NS | Link-Local Multicast Name Resolution and NetBIOS Name Service are vulnerable to responder attacks (name resolution poofing) and should be disabled in domain environments. | GPO (LLMNR): Disable the Multicast Name Resolution Protocol (LLMNR) and set it to Enabled . Network adapters: Disable NetBIOS (TCP/IP settings). |
| Remove Telnet/FTP Server | These unencrypted server components are outdated and insecure. | PowerShell: Uninstall-WindowsFeature -Name Telnet-Server, Web-Ftp-Server -Remove |
B. Enforce Security (SMB Signing & Encryption)

Enable mandatory SMB signing and encryption to ensure traffic integrity and confidentiality and prevent man-in-the-middle (MITM) attacks.
| Hardening Test Point | Objective | PowerShell Measure (Server Configuration) |
| SMB Signing | Ensures that the transmitted packets have not been tampered with (data integrity) and thus prevents session hijacking. | Set-SmbServerConfiguration -EnableSecuritySignature $true |
| SMB Encryption | Ensures that the data cannot be read during transmission (end-to-end confidentiality). | Set-SmbServerConfiguration -EncryptData $true |
C. Set Windows Defender Firewall (WDF) restrictive

The WDF must enforce the Zero Trust principle at the host level.
The default setting should be: Reject anything that is not explicitly allowed.
1. Rule-based hardening and default behavior
The default behavior of the firewall must be set to the most restrictive setting to enforce an “implicit reject” policy.
| Hardening Test Point | Technical Imperative | PowerShell / GPO measure |
| Set default behavior | The default inbound traffic rule must be set to Block (Block). This is the foundation for Zero Trust. | GPO: Computer Configuration > Guidelines > Windows Settings > Security settings > Windows Defender Firewall with advanced security > Windows Defender Firewall features > Set incoming connections to Block (default ). |
| Rule-based hardening | Allow only the ports and protocols (e.g. 3389 RDP, 443 HTTPS, 5985/5986 WinRM) that are absolutely necessary for the server role. | PowerShell (example of RDP): New-NetFirewallRule -DisplayName "Allow RDP Inbound" -Direction Inbound -LocalPort 3389 -Protocol TCP -Action Allow -Profile Domain |
| Outbound traffic | Outgoing connections should also be set to block if possible to prevent malware from “calling home”. | GPO: Firewall Properties > Set outbound connections to Block (default ). In this case, DNS (53), NTP (123) and, if necessary, proxy/WSUS access must be explicitly allowed. |
2. Protocol, port and process restriction
Rules should be designed to be as granular as possible to further minimize the attack surface. The mere port specification is not sufficient.
| Hardening Test Point | Technical necessity | PowerShell / GPO measure |
| Process path constraint | The rule must restrict not only the port, but also the process path of the service (e.g svchost.exe . or w3wp.exe). | GPO: In the Firewall rule, under Programs and Services , specify the full path. |
| Local IP Restriction | If a server has multiple IP addresses, the rule should only be applied to the one through which the service is supposed to communicate. | PowerShell (example): -LocalAddress 192.168.1.100 to the rule. |
| Source IP Restriction | For management ports (RDP, WinRM, SSH), access must be restricted to the IP addresses of the administrators or management jump servers. | PowerShell (example): -RemoteAddress 10.0.0.10, 10.0.0.11 to the rule. |
| Disable unnecessary default rules | By default, Windows enables many rules (such as file and printer sharing or Windows Media Player) that must be disabled on a hardened server. | PowerShell (disabling a rule group): Disable-NetFirewallRule -DisplayGroup "File and Printer Sharing" |
3. Central control and auditing
| Hardening Test Point | Technical necessity | PowerShell / GPO measure |
| Centralized Control (GPO) | Group Policy must be used for consistent and non-tamperable configuration across the entire server fleet. | Create a dedicated server hardening GPO that enforces firewall settings. |
| Enable firewall logging | Logging of dropped (blocked) packets must be enabled to detect attack attempts and optimize the rules. | GPO: Firewall Properties > Logging > Log dropped packets set to Yes . |
4. Advanced hardening with IPsec (Optional but recommended)
For maximum security, the IPsec functionality of Windows Defender Firewall (WDF) can be used to enforce authentication and encryption at the network level. IPsec is typically configured through Group Policy (GPOs) to ensure a consistent policy across the network.
| Hardening Test Point | Technical Imperative | GPO Measure |
| Enforce Domain Isolation | Specifies that a server communicates only with devices that can authenticate as domain members . Unauthenticated hosts (such as guests or unmanaged devices) are blocked. | GPO: Create an isolation policy (Connection Security Rule) in the WDF that allows inbound and outbound traffic only from authenticated domain members (using Kerberos V5). |
| Server isolation (host-to-host) | Communication between critical servers (e.g., web servers and database servers) must be encrypted and authenticated, regardless of the application (defense-in-depth). | GPO: Create dedicated IPsec rules between server roles that require authentication and encryption for all relevant IP traffic (e.g., port 1433 for SQL). |
| End-to-end encryption | IPsec is used to encrypt all IP traffic between two or more servers, which guarantees the confidentiality of the traffic. | GPO: In the connection security rules , set the option to Request encryption or Encryption optionally (depending on the isolation zone). |
| Secure authentication method | IPsec connections must use the most secure method available to authenticate the remote station. | GPO: Using Kerberos V5 (domain credentials) as the preferred authentication method. The use of Pre-Shared Keys (PSK) should be avoided. |
3. Local Policies and GPO Hardening

Group Policy Objects (GPOs) are the central, scalable control element of your hardening process.
They ensure that critical security settings are consistently and enforced across all servers.
A. Password and Account Policies (Domain Level)

These policies are applied at the domain level and are fundamental to protecting user credentials.
| Minimum length | Set the minimum length to at least 14 characters (or more, ideally 16+) to make brute force attacks more difficult. | Password must be at least long: Mindestens 14 Zeichen |
| Complexity | Password complexity must be enabled to enforce the use of digits, special characters, uppercase and lowercase letters. | Password must meet the complexity requirements: Aktiviert |
| Course | Passwords must differ significantly to prevent easy “switching back” to old passwords. | Number of saved passwords: Mindestens 24 Kennwörter |
| Account Suspension (Limit) | After a small number of failed attempts (e.g., 5), immediately suspend the account to block brute force attacks. | Account lockout threshold: 5 ungültige Anmeldeversuche |
| Account suspension (duration) | The duration of the ban must be sufficiently long to stop automated attacks (e.g. 30 minutes). | Duration of account suspension: 30 Minuten |
B. Critical Security Settings (Computer Configuration)

Apply these essential GPOs to the server OU to maximize host security.
| GPO Setting | Path (Security Settings) | Recommended action | Purpose |
| Audit Policy | Advanced Audit Policy Configuration | Enable large-scale successful and failed logins, process creation, and access to objects. | Enables detailed forensics and capture of all relevant security events. |
| User Rights Assignment | Local Policies/User Rights Assignment | “Allow login locally” to and Administratoren Domänen-Admins restrict. Remove Benutzer and Gäste. | Minimizes the possibility of unauthorized local console logins. |
| FIPS Algorithms | Local Policies/Security Options | Enable “System Cryptography: FIPS-Compliant Algorithms…“. | Enforces the use of FIPS (higher security) cryptographic algorithms. |
| Devices: Storage of LM hash values | Local Policies/Security Options | Disable. | Prevents the storage of the weak LM hash, which is easy to crack. |
| Network Security: LAN Manager Authentication Level | Local Policies/Security Options | Click “Send NTLMv2 responses only. LM and NTLM” (Level 5). | Increases the security of NTLM authentication and blocks outdated protocols. |
C. Hardening of Remote Interfaces and Clients

To further reduce the attack surface, the server’s communication mechanisms must be restricted.
| Remote Desktop (RDP) – NLA | Force the use of Network Level Authentication (NLA) to require authentication before starting a full RDP session (protection against DoS/DoS-like attacks). | GPO: Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security > Allow remote connections only from computers that are performing network-level authentication to Enabled . |
| RDP – Access Group | Restrict access to RDP to a dedicated RDP user group (Remotedesktopbenutzer) instead of allowing access to all administrators by default. | GPO: Computer Configuration > Windows Settings > Security Settings > Local Policies > Assign User Rights > Allow Remote Desktop Services Logon to Restrict to the Dedicated Group. |
| NetBIOS Disable | Disable NetBIOS on the network adapter, as NetBIOS information helps attackers with network reconnaissance (part of the LLMNR/NBT-NS measures). | Network adapter setting: TCP/IP v4 Properties > Extended > WINS > NetBIOS over TCP/IP Disable Set. |
| SMB Client Deactivation | If a server does not require outbound connections over SMB (port 445) (e.g., does not mount network drives), the SMB client should be disabled to make lateral movement more difficult. | Registry/GPO: Setting the Registry Value DependOnService for the service LanmanWorkstation (workstation service) to only NlaSvc (instead of Bowser, MRxSmb10, NlaSvc). This requires separate registry interventions via GPO. |
| GPO Management Hardening | The Group Policy Management Console (GPMC) must only be managed from highly privileged accounts from hardened workstations (PAWs) to prevent domain security compromise. | Organizational measure: Implementation of the PAW concept (Privileged Access Workstation). Technically through tiering models and strictly limited GPO editing rights. |
4. Active Directory (AD) Hardening: The Crown Jewels

Active Directory Domain Controllers (DCs) are the highest protection target (Tier 0). A compromise of the DC means the immediate takeover of the entire domain (domain dominance).
Hardening must be particularly rigorous here, as a DC stores all authentication secrets.
A. Role Separation & Physical Isolation
A domain controller should never take on a secondary role (e.g., file server, web server, application host).
It must be strictly isolated to limit the attack surface to the essential DC services.
| Administration isolation | DCs must be managed from dedicated, hardened admin workstations (PAWs/SAWs) or secured JEA sessions, not standard client workstations. | Organization/Process: Implementation of Tier 0 administrators and PAWs. |
| Network isolation | DCs must operate in a dedicated, highly segmented network area (e.g., their own VLAN), with communication strictly limited to necessary protocols (Kerberos, DNS, LDAP, SMB for replication). | Firewall/Network: Detailed WDF rules and network segmentation (VLANs/microsegmentation). |
B. Implementing the tiering model: The supreme discipline
This model architecturally separates the management of critical resources to prevent lateral movement by attackers.
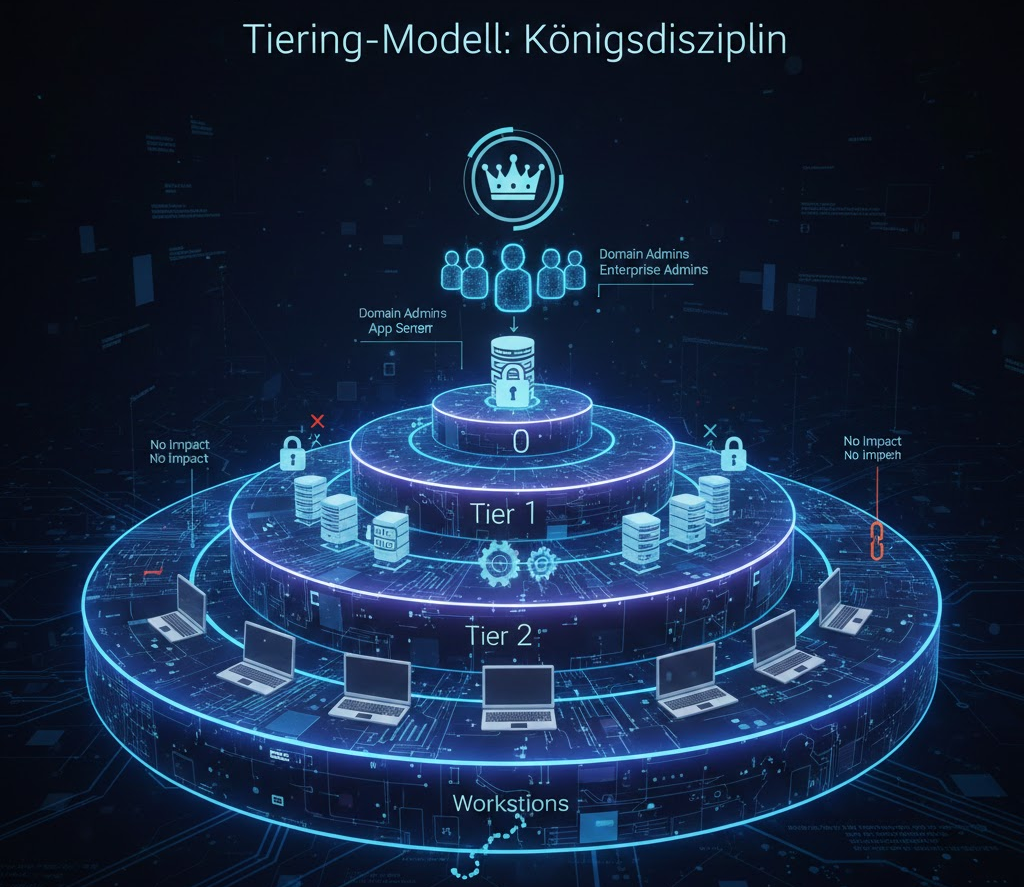
| Tier 0 | Highest control: Domain controllers, domain admins, enterprise admins. | Accounts are never allowed to log in to Tier 1 or Tier 2 systems. |
| Tier 1 | Critical servers: application servers, member servers, database servers. | Local admins of this tier must not have any rights in Tier 0. |
| Tier 2 | Standard clients (workstations). | The compromise of a Tier 2 system must not have any impact on Tier 0 or Tier 1. |
💡 Protection against Credential Theft “Protected Users” Protected Users prevents the storage of cached credentials and the use of the insecure NTLM protocol. Use this group for critical accounts such as domain administrators and service accounts. Important note Ensure that all systems and applications that use these accounts fully support Kerberos and AES before moving accounts to this group.
C. Hardening of Domain Controllers (GPO Base)
Apply additional hardening GPOs specifically to the Domain Controller Organizational Unit (OU):
| LDAP Signing and Channel Binding | Prevents MITM attacks on LDAP communications. | GPO: Set “Domain Controllers: LDAP Server Signing Requests” to Require Signature . |
| Mitigating Kerberos RC4 | Disable support for the weaker RC4 Kerberos encryption type in favor of AES-256 (AES Kerberos Encryption). | GPO: Computer Configuration > Guidelines > Windows Settings > Security settings > Local Policies > Security options > Network Security: Configure encryption types that are allowed for Kerberos (enable AES types only). |
| Anonymous access | Prevent anonymous RPC access to the DC and set the GPO. | GPO: Set Network Access: Restrict Anonymous Access to Shares and Pipeline Names to Specific Restrictions . |
| AdminSDHolder (Protection) | Ensures that the ACLs of privileged accounts cannot be permanently tampered with. The system resets the permissions every hour. | Monitoring: The ACL of the AdminSDHolder object itself needs to be backed up. |
D. Monitoring and hygiene of privileged groups

Verification of privileged group memberships is an ongoing process.
| Regular audits | Regularly review the composition of the most important groups (Domain Admins, Enterprise Admins) and document any deviations. | PowerShell: Get-ADGroupMember -Identity "Domain Admins" |
| Saved Passwords (LAPS) | Implement Local Administrator Password Solution (LAPS) on all member servers (Tiers 1 and 2) to ensure unique local administrator passwords. | Tool: Provision of the LAPS client-side extension and configuration of the associated GPO. |
| Tool Tip for AD Audits | Use specialized PowerShell tools such as easyADReport to automate and generate structured reports on critical AD settings and group memberships. | Tool: Use of dedicated AD reporting tools. |
5. Patch and Update Management: The Endurance Run

An unpatched server is like a castle with an open gate. Patch management isn’t just important, it needs to be automated, mandatory, and fast .
The delay in installing critical updates is one of the most common causes of security incidents.
A. Automation and Compliance
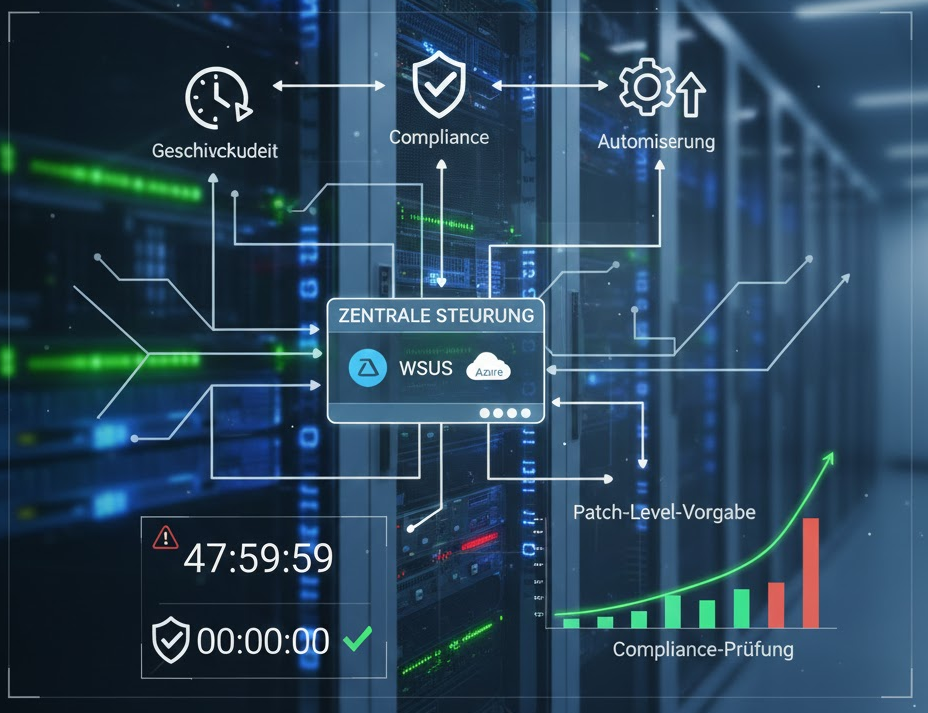
To ensure the security and stability of a server, patch management must move from a manual process to an automated and centrally controlled process .
| Centralized control | Use WSUS (Windows Server Update Services) or Windows Update for Business to ensure centralized control and release of updates. | System: Implementation of WSUS / ConfigMgr / Azure Update Management. |
| Speed (Critical Updates) | Critical security updates (Severity High/Critical) must be installed within 48 hours of release. | Process: Schedule dedicated, automated maintenance windows and immediate rollback capability. |
| Audit (Compliance) | Verify that the servers have reached the defined patch level target through compliance checks. | Tool: Use of Configuration Management solutions or the Security Configuration Analyzer (part of the Microsoft Security Baselines). |
B. Service and Driver Updates

Patch management must not be limited to the operating system (OS); rather, it must take a holistic approach to secure the entire digital infrastructure.
| Firmware and Hypervisor | Keep the firmware (BIOS, RAID controller) and hypervisor (if the server is virtualized) up to date to fix hardware vulnerabilities. | Process: Use of the update tool of the respective hardware manufacturer (e.g. Dell OME, HPE OneView). |
| Third-party software | Implement a process to update critical third-party software (e.g., Java, backup agents) in a timely manner. | Tool: Use of a dedicated third-party patch management tool. |
6. Logging and Monitoring: The Early Warning Systems

The basic principle of cybersecurity is that you can only protect what you see.
Comprehensive logging and real-time monitoring are therefore the indispensable basis of every forensic analysis and incident response (IR) process.
A. Enable Advanced Auditing

In fact, the default Windows audit log is often insufficient for forensic purposes because it only logs basic events.
To ensure complete proof of system activity and perform effective forensic analysis, you need to use the advanced audit guidelines to collect forensically actionable data .
| Logon/Logoff | Enable successful and erroneous logins to detect lateral movement. | PowerShell: auditpol /set /category:"Logon/Logoff" /success:enable /failure:enable |
| Detailed Tracking (Process Creation) | Turn on process creation monitoring. This logs every process startup, which is essential for malware detection. | GPO: Computer Configuration > Guidelines > Windows Settings > Security settings > Advanced audit policy configuration > Detail tracking > Monitor process creation for success and failure . |
| Object Access | Monitor access to critical folders (e.g., System Volume Information, Netlogon, or sensitive data shares). | GPO/SAC-L: Set system access control lists (SACLs) on critical objects. |
| Time synchronization | Make sure timestamps are consistent to allow for the correlation of logs. | GPO: NTP client settings point to the domain controller or a secured source. |
B. Central SIEM System and Log Forwarding
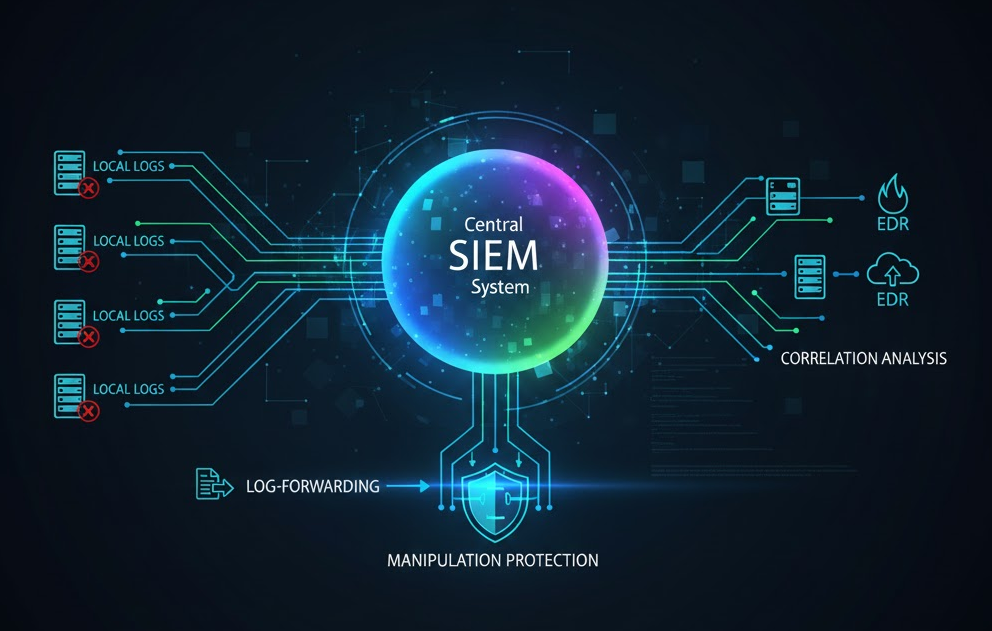
Local logs are easy for attackers to manipulate – they are often deleted, overwritten, or modified once an attacker has gained administrative access to the system.
The reliable solution for this is central aggregation.
| Log Forwarding | Forward all logs (especially the security logs) to a central SIEM ( Security Information and Event Management) system immediately after they are created. | Tool: Use of Windows Event Forwarding (WEF) or a third-party agent. |
| Tamper protection | By forwarding immediately, you prevent an attacker from deleting or manipulating local logs. | Objective: Secures the forensic chain of evidence. |
| Correlation analysis | In the SIEM system, the protocols can be correlated with other sources (firewalls, EDR data). | Objective: Real-time threat detection and identification of complex attack patterns. |
7. File system and registry hardening

These measures aim to maximize local data security , ensure the integrity of critical system components, and rigorously stop commonly used malware persistence mechanisms .
A. File System and Folder Permissions (NTFS)
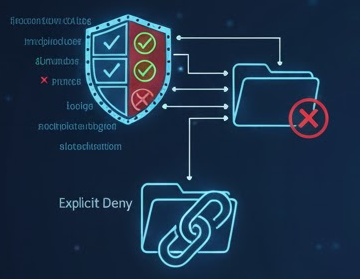
File system hardening focuses on access control lists (ACLs) and restricting execution mechanisms to prevent compromised users or processes from causing damage or spreading.
| NTFS-PoLP | Implement strict access control lists (ACLs) permissions that allow only the service account and administrators to access application files or logs. | Manual configuration/scripting: Use explicit permissions instead of inheritance and explicit deny (Explicit Deny) for unauthorized groups (e.g. “Everyone”). |
| Disable inheritance | Disable the inheritance of permissions for critical folders (e.g. program files) and define static, strict permissions. | Tool: icacls <Pfad> /inheritance:d (Disable Inheritance). |
| Disabling 8.3 filenames | Prevent the generation of short DOS-compatible file names. This prevents some attacks and increases performance. | Registry/CMD: fsutil 8dot3name set 1 (Disable on all drives except system drive). |
B. Registry Hardening and Persistence
The Windows Registry is a primary target for persistence and disabling security settings by malware.
| AutoRun deactivation | Prevent removable media (USB sticks) from executing programs automatically, a classic attack vector. | GPO: Computer Configuration > Administrative Templates > Windows Components > AutoPlay > Policies Disable Autoplay Set to Enabled . |
| Securing Run Keys | Protect the registry paths used by malware for persistence (Run, RunOnce). | Registry/GPO: Set strict ACLs on the registry keys: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run* and HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run*to restrict write access. |
| Remote Registry Access | Prevent remote access to the registry via the RemoteRegistry service. | Service Setting: RemoteRegistry Set the service to Disabled (see Section 2B). |
8. Local account hardening and administrator hygiene
This section backs up local server accounts to prevent lateral movement .
The strategy includes reducing the attack surface by renaming the administrator account, disabling the guest account, and centralized, unique password management using LAPS.
In addition, the login rights (console and network) are strictly limited to the administrative roles actually required.
A. Back up local administrator accounts
The local administrator and guest accounts are critical attack vectors, especially if they are not standardized, secured, and monitored.
They often serve as a stepping stone for lateral movement in the network or for privilege escalation.
| Account renaming | Rename the default administrator account (for example, to Lokal_Admin_XXX) to make brute force attacks more difficult. | GPO: Local Policies/Security Options > Accounts: Rename administrator account name set to new name. |
| Deactivate guest account | The default guest account must be deactivated. | GPO: Local Policies / Security Options > Accounts: Set Guest Account Status to Disabled . |
| Force LAPS | Implement the Local Administrator Password Solution (LAPS) on all member servers (repeated emphasis). | Tool: Provision of the LAPS client-side extension and configuration of the associated GPO. |
B. Access Control and Permissions
Direct console and network login rights must be strictly restricted .
This is crucial to minimize the attack surface and limit an attacker’s ability to move laterally in the network.
| Console Login | Restrict local console login to the Administrators group to prevent unauthorized local logons. | GPO: Assign user rights > Allow login locally to restrict to the group Administratoren . |
| Network Login | Restrict network login (for services like SMB, WinRM, etc.) to the most critical accounts/groups. | GPO: Assign user rights > to deny Gäste access from the network to this computer and Lokale Konten set it. |
| Deny Blank Passwords | Disable the ability to use blank passwords (relevant for local accounts). | GPO: Local Policies/Security Options > Accounts: Set local accounts empty passwords only to allow console logins to Disabled . |
9. Cryptographic Hardening and TLS/Cipher Suites

Modern servers must rigorously disable outdated, insecure encryption protocols (such as TLS 1.0/1.1 or weak cipher suites).
This is a fundamental requirement of hardening to ensure the confidentiality and integrity of all server communications.
A. Protocol Deactivation
| TLS 1.0 and 1.1 | Disable support for TLS 1.0 and 1.1, as these protocols are considered insecure (e.g., vulnerable to BEAST attack). | Registry: Set DisabledByDefault on 1 and Enabled on 0 under the respective TLS version subkeys (HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client and \Server). |
| SSL 2.0 and 3.0 | These protocols must be completely disabled. | Registry: Analogous to TLS deactivation, but here the deactivation of the entire protocol folder is often sufficient. |
B. Cipher Suite Preference
| Cipher Suite Order | Enforce a preference for strong, modern ECDHE/AES-256-GCM cipher suites and disable any weak or insecure ciphers (e.g. 3DES, RC4). | PowerShell: Get-TlsCipherSuite for examination. GPO: Computer Configuration > Administrative Templates > Network > SSL Configuration Settings > SSL Cipher Suite Order (Define and Sort by Strength). |
| Disable RC4 cipher | RC4 must be removed from the cipher suite list. | GPO: Use the SSL Cipher Suite Order to ensure that RC4 suites are missing or explicitly blocked via registry entries. |
10. Additional protection mechanisms: The special tools

These mechanisms are key to defending against modern, in-memory attacks ( pass-the-hash) and enforcing the principle of least privilege at the application level.
They complement basic hardening and provide in-depth protection against advanced threats.
A. Credential Guard (Schutz vor Credential Theft)
| LSASS insulation | Credential Guard protects sensitive credentials (hashes, TGTs) and the Local Security Authority Subsystem Service ( LSASS) process by running it in an isolated, virtualization-based environment (VBS). | Even if the kernel on the host is fully compromised, attackers cannot extract the credentials from the protected LSASS memory (highly effective against Mimikatz). |
| Prerequisites | Enable Virtualization-Based Security (VBS). | Requires UEFI, Secure Boot, and Virtualization (Hyper-V) components. |
B. Application Control: AppLocker & Windows Defender Application Control (WDAC)
| Application Whitelisting | Only the execution of explicitly approved applications, scripts and DLLs is allowed. | This is one of the most effective defenses against ransomware or unknown malware running. |
| WDAC (Windows Defender Application Control) | Modern, more secure variant based on kernel-level code integrity policies. | Should be preferred in highly secure environments. |
| AppLocker | Well suited for smaller, static environments to restrict executables, scripts, and MSI installers via Group Policy. | Easier to implement than WDAC, but less tamper-resistant. |
C. Just Enough Administration (JEA)
| PoLP for Administration | JEA enforces the principle of least privilege at the management level by allowing administrators to execute only the minimum necessary PowerShell commands. | Administration is carried out via a secure PowerShell remoting session. The user can only perform defined role capabilities . |
| Procedure | The actual execution takes place under a non-privileged service account. | Define the allowed cmdlets and functions in a .psscfile and register the session configuration. |
D. Device Guard (Code Integrity Policy)
| Code Integrity | Ensures (implemented by WDAC) that the system only runs code that is signed or whitelisted by a trusted publisher. | This prevents attackers from loading unsigned or manipulated code (such as drivers) at the kernel level. |
| Policy Protection | Protect the WDAC policy itself so that it can’t be tampered with by local administrators. | GPO/Registry setting for WDAC policy protection. |
Hardening automation and community tools

Manually applying all hardening measures is time-consuming and error-prone. Modern security is based on the automation of these processes.
The following projects provide ready-to-use scripts and configurations for fast hardening of Windows servers.
| Microsoft Security Baselines | Official Microsoft Desired State Configuration (DSC) configurations to implement Microsoft’s recommended security baselines via GPOs or DSC. Ideal for consistency and compliance. | https://github.com/microsoft/Security-Baseline |
| PhinIT easyADReport | Comprehensive PowerShell reporting tool for Active Directory auditing, security analysis, and compliance monitoring. | https://github.com/PS-easyIT/easyADReport |
| PhinIT easyConnections | PowerShell tool with WPF GUI for real-time monitoring and analysis of network connections on the host (debugging the WDF rules). | https://github.com/PS-easyIT/easyConnections |
| CIS-CAT Pro (Benchmarks) | Provides automated scanning and configuration checks against the Center for Internet Security (CIS) benchmarks, an industry standard for server hardening. | https://www.cisecurity.org/cis-benchmarks/ |
| NSCB (NCSC Windows 10/Server) | A collection of GPO proposals and scripts from the National Cyber Security Centre (UK) for hardening Windows operating systems. | https://github.com/ncsc/device-security-guidance |
| PowerShell Hardening (Miscellaneous) | Various PowerShell modules and scripts that automate specific hardening tasks (e.g. disabling legacy protocols). Here you can often find smaller, focused scripts from community developers. | https://github.com/topics/windows-hardening |
Hardening as a continuous process

A hardened Windows Server is not a one-time project, but a continuous process. The measures described here drastically reduce the attack surface and create a robust security architecture.
Your benefit as an administrator : Less risk, higher compliance and a system that can withstand even modern attack techniques.
Invest time in automation and monitoring, that’s the key to sustainable security. With consistent hardening, you not only achieve protection, but also stability and trust in your critical infrastructure.
PowerShell Tools
easyConnections is a powerful PowerShell tool with a WPF graphical user interface for monitoring and analyzing network connections in real time. The tool is designed for advanced network diagnostics and security monitoring.
- Real-time monitoring of TCP and UDP connections
- Color-coded categorization by service type (web, email, database, etc.)
- Recording function to collect connection data over time
- HTML export for reports and documentation
- Advanced filtering by protocol, direction, and category
easyADReport is a comprehensive PowerShell-based Active Directory reporting tool with a modern WPF interface. It provides over 80 pre-built reports for auditing, security analysis, and compliance monitoring of your Active Directory environment.
- 80+ pre-built reports: Comprehensive coverage of AD objects and security configurations
- Modern WPF interface: Clean, intuitive Windows 11-style user interface
- Real-time analysis: Instant reporting without database requirements
- Export functions: Export the results to CSV, Excel, HTML or PDF
- Advanced Filtering: Powerful search and filter options for all reports
- Security-focused: Comprehensive security analysis and vulnerability detection
- No dependencies: Works with standard PowerShell and AD modules






Be the first to comment